Security controls validation
Validate and enhance your security posture
DEFINITION
Why Security Controls Validation?
Your organization’s security controls are fundamental to your defense against cyber threats. But in a rapidly evolving landscape, are you sure that they are providing the level of protection you need to safeguard your most critical assets?
To minimize the risk of serious breaches and demonstrate assurance, testing the performance of your controls on a regular basis through security controls validation is now considered vital.
BE THREAT-CENTRIC AND PROACTIVE
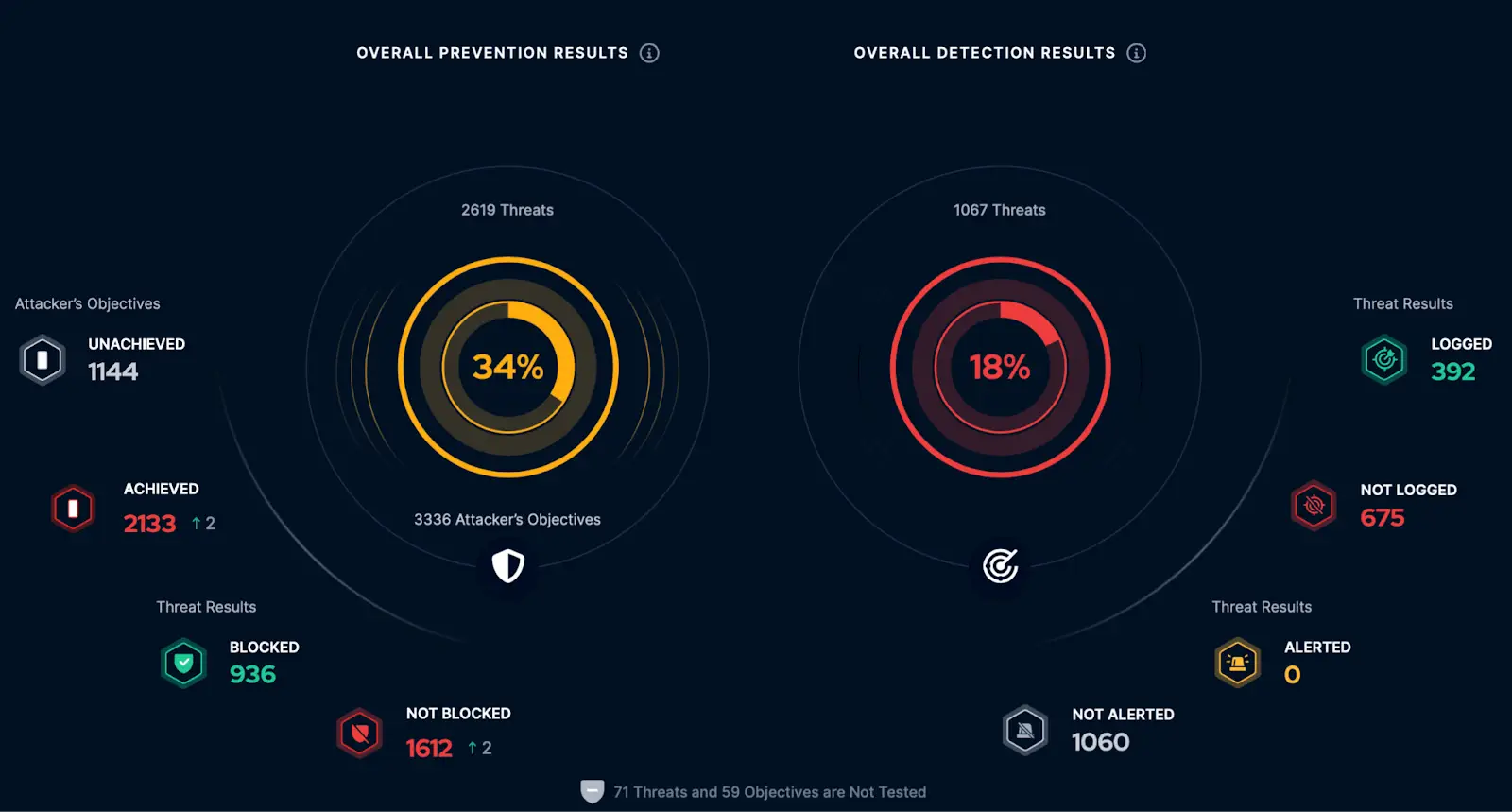
Satius Security Controls Validation (SCV) is a Breach and Attack Simulation (BAS) service that helps you to measure and strengthen cyber resilience by automatically and continuously testing the effectiveness of your security tools.
With Satius SCV simulate real-world cyber threats to identify prevention and detection gaps, and obtain actionable mitigation recommendations to address them swiftly
and effectively.
Tests security controls continuously, 24/7
Simulations identify threat prevention and detection weaknesses by assessing the effectiveness of your security tools via continuously scheduled simulations.
Validates preparedness against the latest threats
With a rich threat library, updated daily by offensive security experts, Picus tests your defense against current and emerging attack techniques.
Optimizes prevention and detection capabilities
To achieve optimal protection from your security tools, Satius supplies easy-to-apply prevention signatures and detection rules.
Operationalizes MITRE ATT&CK
Satius maps assessment results to the MITRE ATT&CK Framework, enabling you to visualize threat coverage and prioritize mitigation of gaps.
Evidences the value of investments
Supplying real-time metrics, including an overall security score for your organization, Picus helps you to measure performance and prove value.
Improves SOC efficiency and effectiveness
Satius automates assessment and engineering processes to reduce fatigue and help your security teams work together more collaboratively.
OVERVIEW
HOW IMPROVES YOUR SECURITY POSTURE
Have your security controls been tested? Do you know if they are ready to respond effectively to today’s attack patterns? Satius Security Breach & Attack Simulation platform combines the expertise, best tools, and the MITRE ATT&CK framework to perform customized simulations to your environment.
With deep knowledge of the industry, market and geographical factors which influence the threat landscape, we craft a series of highly trackable and repeatable breach simulations to prepare your systems and teams for likely threats. Combined with any specific requirements your organization may have, we will layer industry standards and years of experience to help test your ability to detect and respond to indicators throughout the kill chain. We will then support your organization in identifying and prioritizing next steps for your security team.
- Measure and optimize the protection provided by existing security controls
- Discover and eliminate attack paths to critical systems and users
- Optimize detection and response capabilities to eliminate attacks sooner
KEY FEATURES
SECURITY CONTROLS VALIDATION TO PROVIDE ASSURANCE
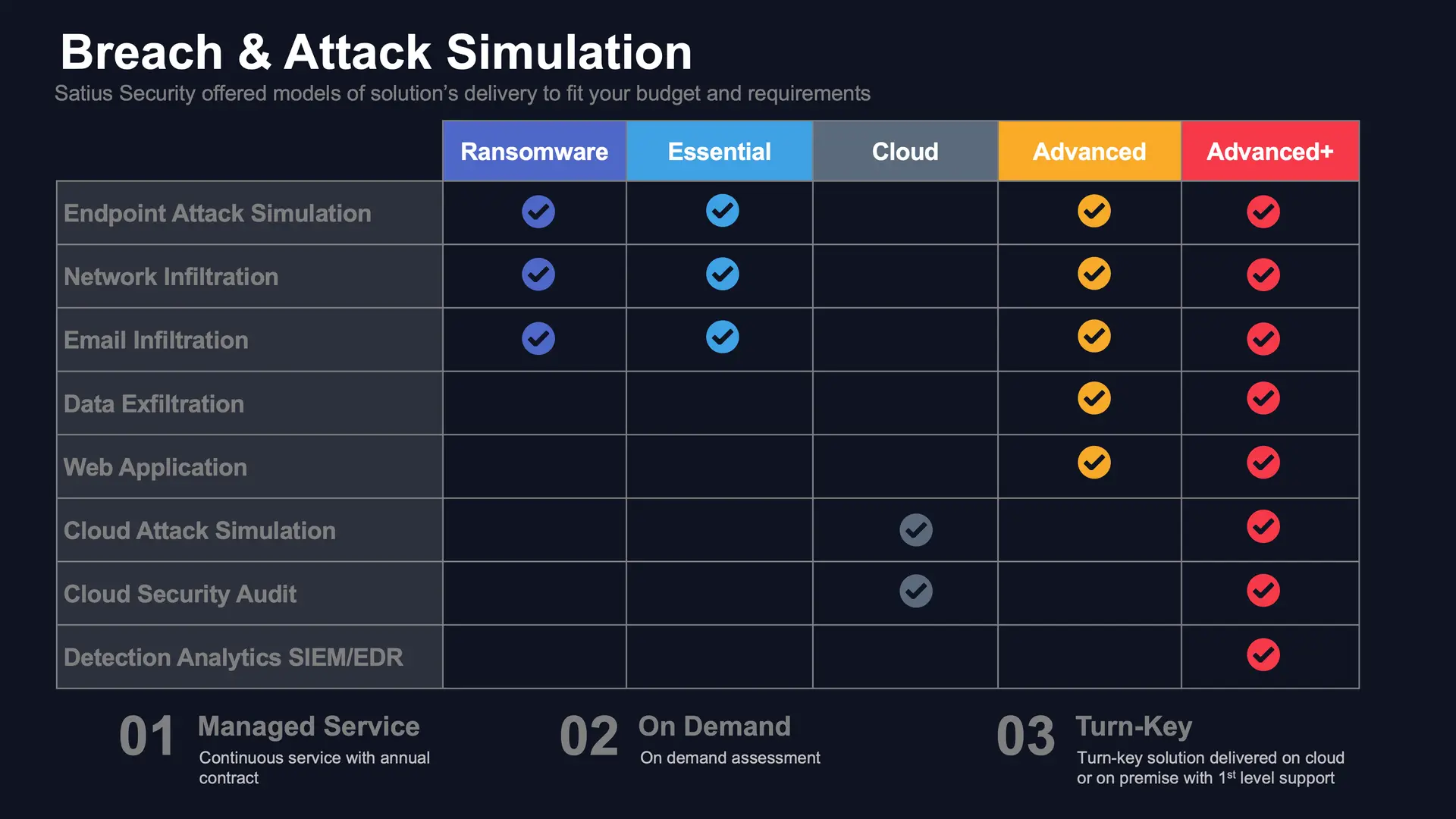
Security Controls Validation, takes Breach and Attack Simulation to the next level.
Depending on the service model selected or a turn-key solution delivery, modules provide the end-to-end capability you need to simulate threats, validate effectiveness, and mitigate gaps – safely, simply and continuously.
- An extensive library of 4,000+ threats consisting of 20,000+ actions, updated daily
- Simulates attacks instantly or per a predefined schedule
- Individually customizable threats and attack scenarios
- Compare your security scores with industry peers, regional counterparts, and other Picus users.
- Over 70K+ prevention signatures and detection rules
- Validates network security, SIEM & EDR tools
- Maps results to MITRE ATT&CK
- Executive dashboards and reports
- Supports Windows, Linux and macOS
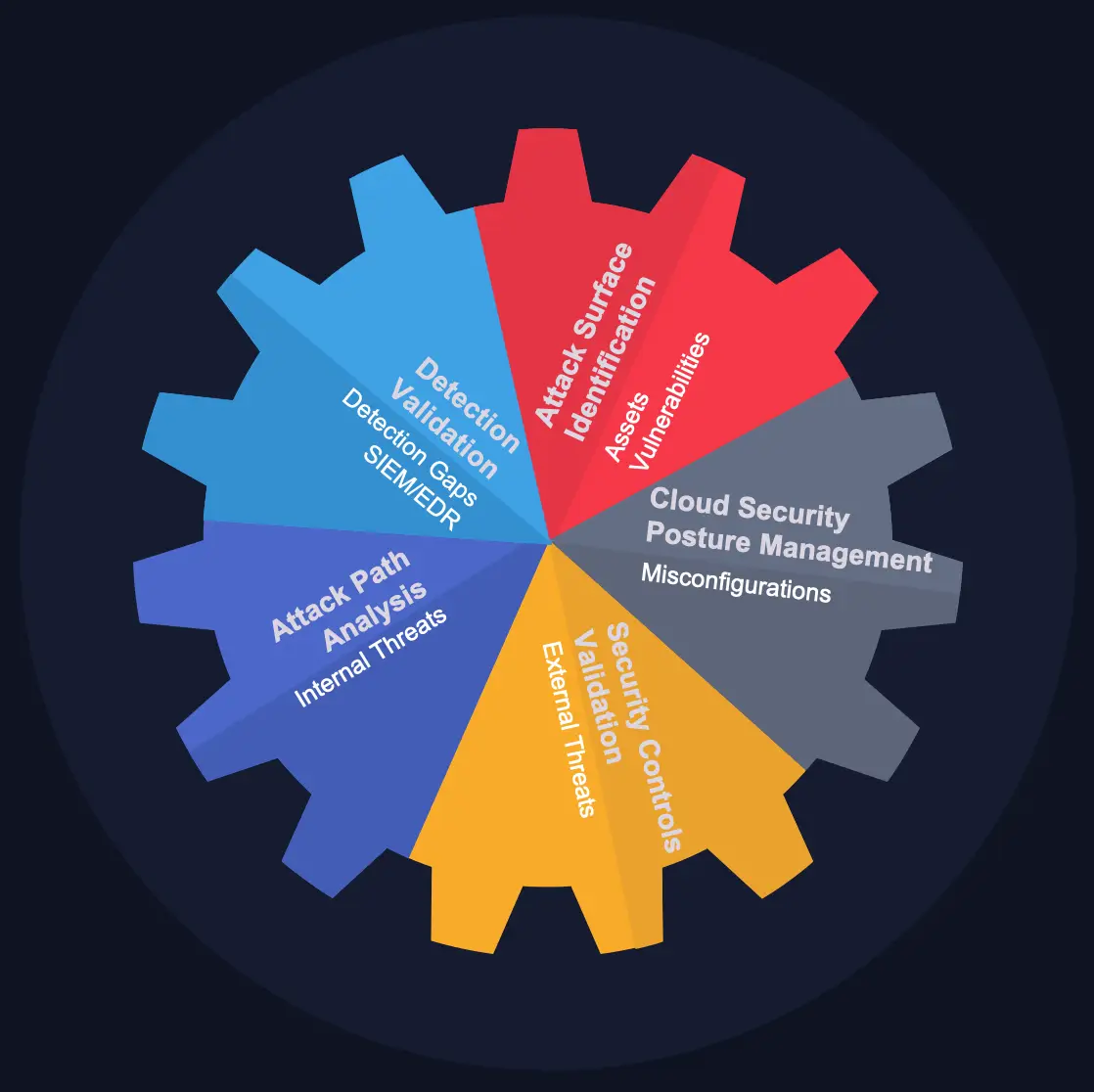
How Satius offers BAS services
CAPABILITIES
What Types of Security Controls Can Be Tested with (BAS)?
Breach and Attack Simulation (BAS) can assess a wide range of security controls across an organization’s infrastructure, helping to identify potential weaknesses and improve overall security posture. Some of the security controls that can be tested with BAS include:
BAS can simulate attacks that target Next-Generation Firewalls (NGFW), Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS), Web Application Firewalls (WAF), and network segmentation.
This assessment focuses on automated behavioral detection (EDR), signature-based detection (anti-virus), known vulnerabilities and patches on various tools including Windows and 3rd-party software, hardening of your endpoints, Ransomware, etc.
software, hardening of your endpoints, Ransomware, etc.
BAS can simulate malware and ransomware infections to test the effectiveness of anti-malware and antivirus solutions, Host-based Intrusion Prevention Systems (HIPS), Endpoint Detection and Response (EDR) solutions, and host-based firewalls. This may involve attempting to execute malicious payloads on endpoints or attempting to disable security software.
By sending simulated phishing emails with malicious attachments or links, BAS platforms can test the organization’s email filtering systems, email gateway security, spam filters, and anti-phishing measures.
BAS can attempt to bypass Multi-factor Authentication (MFA), exploit weaknesses in role-based access control (RBAC) configurations, or test the resilience of identity and access management (IAM) solutions by simulating credential-based attacks.
BAS can exploit known vulnerabilities in software and systems to test the effectiveness of patch management processes, software and hardware inventory management, and vulnerability scanning solutions.
By simulating attempts to exfiltrate sensitive data, BAS can test the effectiveness of Data Loss Prevention (DLP) solutions, encryption technologies, and secure storage configurations. This may include simulating file transfers, database breaches, or unauthorized access to sensitive information.
BAS can generate simulated security incidents to test the organization’s Security Information and Event Management (SIEM) solutions, log management systems, and incident response processes. This could involve creating false positive alerts, simulating a data breach, or triggering other security events to evaluate the response time and effectiveness of the incident response team.
Ready for Cyber Resilience?
Learn more how our Managed Service can help you achieve Cyber Resilience and be an extension of your team without breaking the budget.
TESTIMONIALS
What our clients say about us
We work with organisations across a range of industries
- Finance
- Government
- Retail
- Healthcare
- Education
- Industrial
