file integrity monitoring
Gain confidence in systems integrity
Overview
Secure critical IT systems and prove compliance
As industry regulations expand in scope and complexity, organizations need solutions that simplify the process of securing, monitoring and validating the configuration of critical systems. A strong compliance posture starts with secure systems configurations coupled with intuitive detection of unauthorized changes. With security configuration management and change control software, you can significantly reduce your organizations attack surface, detect & remediate breaches and pass compliance audits more easily.
Establish strong configurations and maintain system integrity
Enhance breach forensics with constant monitoring and verification
Increase confidence in your security posture and ability to prove its strength
SCOPE
Harden the security configuration of your critical information systems
Harden configurations faster
Reduce the effort to establish safe configurations and take the guesswork out of hardening critical systems with customizable build templates from multiple standards bodies, including CIS, DISA STIG and SCAP/OVAL.
Pass security compliance audits with ease
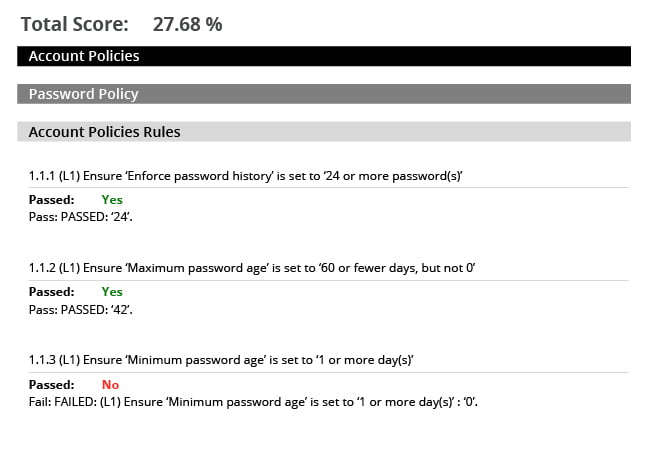
Reduce the effort needed to prove compliance by automating repetitive tasks using 250+ CIS‑certified reports covering NIST, PCI DSS, CMMC, STIG and NERC CIP.
Look back in time
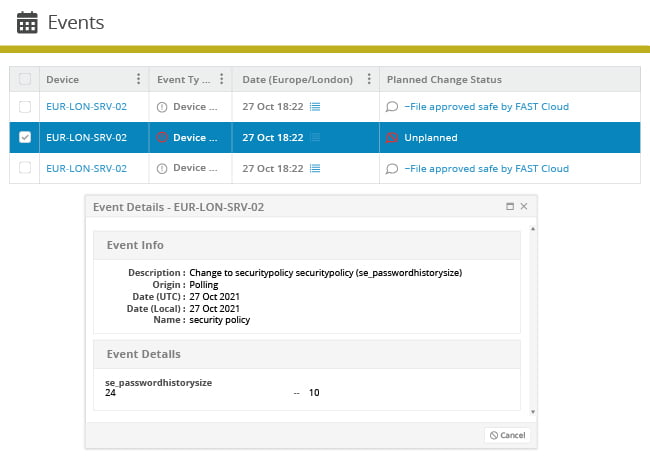
Determine exactly which systems were modified and when by reviewing a complete history of all changes.
Close the loop on change control
Remove noise and empower operations teams to focus on truly anomalous changes by coordinating configuration management activities with your IT service management (ITSM) solution.
Stay informed about your security posture
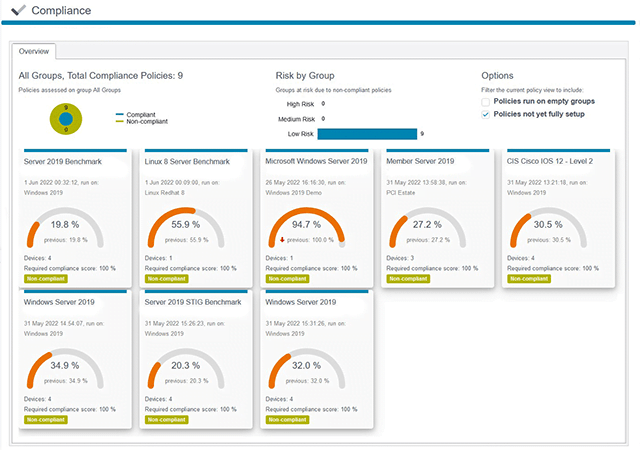
Be confident that your infrastructure and sensitive information are safe by checking the status of your security and compliance posture at any time.
Highly effective file integrity monitoring
Reduce the threat of malware by verifying that your critical systems files are authentic by automatically cross-checking your file integrity monitoring results against a database of over 10 billion file reputations submitted by original software vendors like Microsoft, Oracle and Adobe to ensure all file activity is planned and authentic
Achieve success with regulatory compliance
Navigating industry regulations can be difficult and time consuming without the right tools. Netwrix offers a suite of solutions that address various aspects of regulatory compliance, enabling our customers to succeed in implementing the required security practices and to prove compliance.
Some of the regulations we support include:
- PCI DSS
- RMiT
- SAMA
- NERC CIP
- NIST 800-171 & CMMC
- SWIFT
- NIST 800-53
- HIPPA
- CIS CONTROL
Ready for Cyber Resilience?
Learn more how our Managed Service can help you achieve Cyber Resilience and be an extension of your team without breaking the budget.
