azure cloud security
Cloud security posture validation
OVERVIEW
Cloud Security Validation for Microsoft AZURE
Migration of workloads to the cloud continues to increase the challenge of defending against the latest cyber threats.
Satius Cloud Security Validation helps security teams keep pace with cloud security posture management by identifying common misconfigurations and overly permissive IAM policies – the two primary causes of cloud data breaches.
Through 2025, at least 99% of cloud security failures will be the customer’s fault, mainly in the form of cloud resource misconfiguration.
GARTNER
KEY FEATURES
Challenges of AZURE Cloud Security
To ensure that your cloud workloads in Microsoft Azure are secure, it’s important to assess your environments regularly. Azure cloud attacks occur because organizations fail to follow Microsoft’s Shared Responsibility Model and proactively identify cloud misconfigurations in the services they rely on daily.
Common Azure misconfigurations that can lead to cloud security data breaches include:
- Misconfigured IAM policies
- Unrestricted access to resources
- Insecure data storage
ADDRESS CLOUD SECURITY ISSUES BEFORE THEY LEAD TO INCIDENTS
Due to the rapid pace of digital transformation, the increasing complexity of cloud environments, and human error, critical security gaps that could enable attackers to compromise your cloud services can arise daily.
Satius Security Validation for AZURE helps you to proactively identify and address exposures by:
Auditing core AWS services
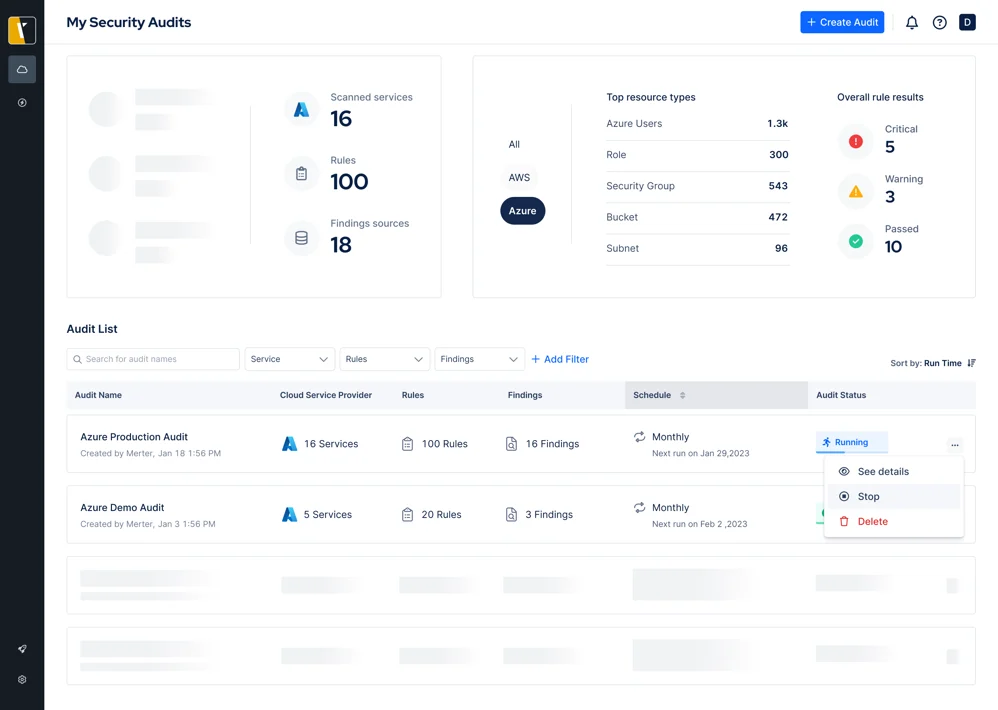
Scanning 16 Azure services, Satius identifies critical cloud misconfigurations that attackers could exploit. These include excessive privileges, unused resources, and cryptographic failures.
Simulating privilege escalation scenarios
In the event attackers are able to access your cloud environment, they will likely attempt to access critical systems by escalating privileges. To identify overly permissive IAM policies, Satius CSV gathers resources from across Azure and simulates attacks in a Local Policy Simulator.
Delivery Models
Our Cloud Security Validation doesn’t just identify issues. It also provides the insights and recommendations you need to understand their severity and respond to risks quickly.
With different and flexible delivery models of our service, we insure clients get the most suitable option for the requirements and the budget.
On-Demand Assessment
Short engagement aimed to validate your cloud security with a executive report and actionable insight findings report.
Managed Service
This continuous service can be offered as a stand alone for cloud security validation or as a part of our broader Continuous Threat Exposure Management CTEM offering.
Turn-Key Solution
Whether you wish to upgrade from on demand or managed service to have the platform delivered from implementation to 1st level support and training.
Our security qualifications
Our experts hold numerous industry certifications and vendor specific certified trainings to insure standardized approach and optimal results.
Ready for Cyber Resilience?
Learn more how our Managed Service can help you achieve Cyber Resilience and be an extension of your team without breaking the budget.
Latest news
Our penetration testing process
Satius’s security penetration testing services are based on a systematic approach to vulnerability identification and reporting. Our advanced pentest methodology includes:
THE OPPORTUNITY TO DEAL WITH CYBER RISKS BEFORE THE ATTACK
Satius leverages both machine learning and an intricate decision engine to identify suspicious DNS queries. When a domain has been flagged as suspicious by the system, it is then moved into the Watch Engine for ongoing monitoring.
WHAT MAKES OUR SERVICE
THE DIFFERENCE BETWEEN VICTIM AND VICTOR
Satius Security watches the Domain Name System (DNS) egress traffic patterns and therefore understands what domains and infrastructure devices inside the enterprise are trying to communicate with. We focus on understanding where and how often devices are trying to communicate with remote domains or pieces of Internet infrastructure, using advanced tools to understand the associated risk, what can be allowed, what needs to be watched and inspected, what should be blocked, and when alerts should be generated.
Key Capabilities
- Blocks malware domains
- Blocks phishing domains
- Malware Domain Generation Algorithm (DGA) protection
- Machine learning to augment threat feeds
- Content filtering
- API access for SIEM integration
- Validates DNSSEC
- DoH/DoT capable
- Customizable policies by group, device, or network
- Deploys across hybrid architectures






