Managed Protective DNS
Managed Protective DNS to Detect, Block, and Disrupt malicious communications.
DEFINITION
WHAT DNS IS
DNS is a fundamental internet protocol that was built for efficiency and scalability — but not necessarily security. The system is designed to fulfill lookups as quickly as possible, with recursive resolvers passing the request along to DNS servers higher up the chain of authority if the information is not stored in their cache.
Recursive resolvers will contact root servers, which will then pass the request to the TLD nameserver responsible for the queried domain’s extension (.com, .net, .uk, etc.). Finally, the request will be routed to the authoritative nameserver for the requested domain, consulting the domain’s A Record to return an IP address.

OVERVIEW
What is Protective DNS
When malware infects a system, it doesn’t act independently. Before it does anything, it needs to talk to an external agent that lies outside of the infected system. It must “beacon out” for instructions.
Protective DNS is a policy-implementing, recursive DNS resolver service built as the successor to the capability currently being delivered by E3A DNS Sinkhole. Protective DNS is deployed upstream of agency networks. The service filters DNS queries - by comparison to a range of unclassified threat intelligence - to prevent resolution for known malicious domains and/or IP addresses. Protective DNS supports emerging DNS technologies including encrypted DNS protocol support (DoH/DoT) and IPv6 resolution. DNS log data is made available to users of Protective DNS to dramatically increase visibility. Additionally, users are able to heavily customize alerts, data extraction, and other system features.
CYBER SECURITY & INFRASTRUCTURE AGENCY (CISA)

KEY FEATURES
Why we need Managed Protective DNS
When malware infects a system, it doesn’t act independently. Before it does anything, it needs to talk to an external agent that lies outside of the infected system. It must “beacon out” for instructions. Protective DNS blocks access to malicious websites, detects and disrupts malicious communication, which can prevent data exfiltration, filter unwanted content, and provide early threat detection capabilities.
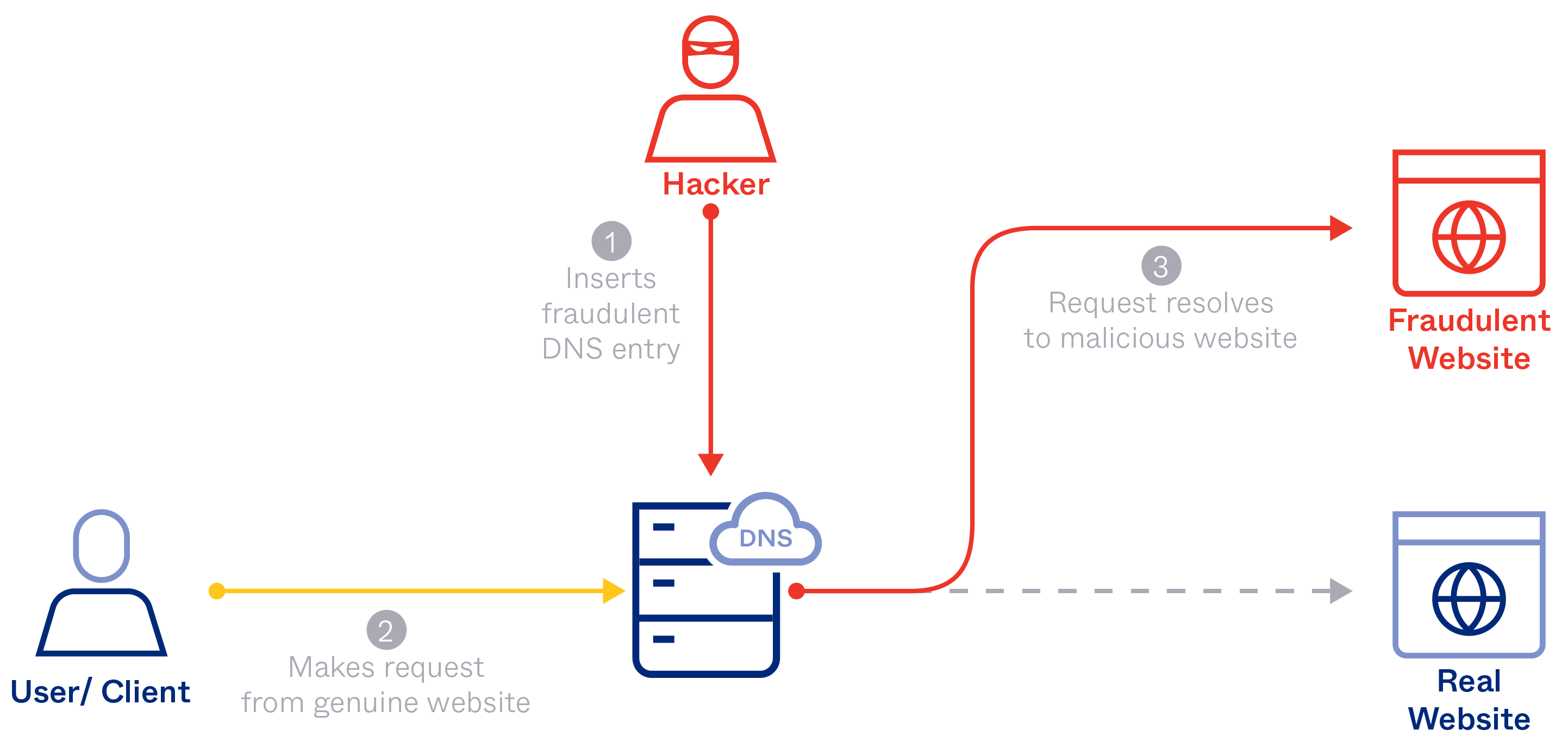
We must assume an organization is already breached – or will be imminently – so the job of Protective DNS is to identify and block communications from adversary infrastructure.
- Helps target organizations understand what’s going on in order to stop malware early in the kill chain
- Stops ransomware attempts by disabling efforts to steal and exfiltrate data from the target organization
- Prevents threat actors who infiltrate organizations from encrypting data or deploying ransomware
- Helps avoid difficult conversations with the board, negative financial fallout and reputational damage
The value of Satius's Managed Protective DNS
Satius Security’s Managed Protective DNS was founded with the mission to learn all we could about adversary infrastructure and then – how to use that knowledge to identify, predict, and ultimately dismantle the attacks associated with that infrastructure.
Our service is powered by a vast graph database that maps what was nefarious yesterday to what is nefarious today to what is being created for nefarious purposes tomorrow. This happens before attacks are launched, enabling organizations to mitigate the damage.
Comprehensive
Looks at domains throughout their whole lifecycle: from birth to abandonment to rebirth.
Real-time
Real-time insight into meaningful, myriad movements and changes across the internet at any second.
Poweful
Has powerful underlying data that backs up the quality of its solution.
Accurate
Characterizes and separates good and bad communication more accurately.
THE OPPORTUNITY TO DEAL WITH CYBER RISKS BEFORE THE ATTACK
Satius leverages both machine learning and an intricate decision engine to identify suspicious DNS queries. When a domain has been flagged as suspicious by the system, it is then moved into the Watch Engine for ongoing monitoring.
WHAT MAKES OUR MANAGED PROTECTIVE DNS THE DIFFERENCE BETWEEN VICTIM AND VICTOR
Satius’s Managed Protective DNS watches the Domain Name System (DNS) egress traffic patterns and therefore understands what domains and infrastructure devices inside the enterprise are trying to communicate with. We focus on understanding where and how often devices are trying to communicate with remote domains or pieces of Internet infrastructure, using advanced tools to understand the associated risk, what can be allowed, what needs to be watched and inspected, what should be blocked, and when alerts should be generated.
Key Capabilities
- Blocks malware domains
- Blocks phishing domains
- Malware Domain Generation Algorithm (DGA) protection
- Machine learning to augment threat feeds
- Content filtering
- API access for SIEM integration
- Validates DNSSEC
- DoH/DoT capable
- Customizable policies by group, device, or network
- Deploys across hybrid architectures
Ready for Cyber Resilience?
Learn more how our Managed Service can help you achieve Cyber Resilience and be an extension of your team without breaking the budget.
TESTIMONIALS
What our clients say about us

Basheer Altayeb
We have been working with Satius for years to understand and minimize risks. The team performed multiple projects from vulnerability management to security controls validation. very satisfied with the value received.

Tedd Long
Partnering with Satius Security has been a game-changer for our organization. Their expert team and proactive approach have provided us with unmatched peace of mind in today's cyber landscape.

Steve Jablonski
Working with Satius Security has been instrumental in bolstering our company's cybersecurity defenses. Their proactive solutions and round-the-clock support have significantly enhanced our resilience against cyber threats. I highly endorse their services to any IT team looking to elevate their security posture.

Elie Hamouche
Satius is a professional IT Security Company that always gives the best value. We benefited from their recommendations and expertise to mitigate findings.
We work with organisations across a range of industries
- Finance
- Government
- Retail
- Healthcare
- Education
- Industrial
Latest news
Use Cases
Our simulation service is designed to test an organization’s security posture by simulating various stages of a cyberattack, from initial compromise to data exfiltration. The primary goal is to simulate the tactics, techniques, and procedures (TTPs) of real-world cyber attackers to validate the effectiveness of your endpoint prevention and detection mechanisms against emerging threats.
Validate Endpoint Security Controls
Validate against advanced threats including emerging threats and ransomware.
Ransomware Readiness
Validate and enhance your ability to defend against the latest ransomware threats, closing security gaps swiftly.
Security Posture Validation
Assess and quantify the effectiveness of security your controls to prevent, detect and respond to attacks across the cyber kill chain.
Cloud Posture Validation
Identify common cloud misconfigurations and overly permissive IAM policies - the two primary causes of cloud data breaches.
