On Demand Assessments
Penetration Testing
Gain independent assurance and support compliance with Expert Led Pen Testing
By proactively identifying and exploiting vulnerabilities and providing clear help and advice to remediate issues, our ethical hacking and security penetration testing services enable you to understand and significantly reduce your organization’s cyber security risk.
Satius Security’s approach ensures the organization’s Technology, Process, and People’s readiness and capacity to disrupt the attack kill chain at every stage.
Our security qualifications
Our experts hold numerous industry certifications and vendor specific certified trainings to insure standardized approach and optimal results.
overview
What is penetration testing?
Penetration testing, or pen testing, is a method in ethical cybersecurity assessment designed to detect and safely exploit vulnerabilities in computer systems, applications, and websites. It mimics real cyber threats by utilizing similar tools and tactics, offering invaluable insights for effective remediation.
- Rapidly fixes vulnerabilities
- Supports compliance requirements
- Provides independent assurance
- Demonstrates security commitment
- Improves cyber risk awareness
- Informs future investments
Types of Penetration Testing We Offer
Network (Internal & External) Testing
Satius conducts thorough investigations of your network to detect and exploit various security vulnerabilities extensively. This process helps us determine if assets, such as data, are susceptible to compromise, assess the risks to your overall cybersecurity, prioritize vulnerabilities for resolution, and suggest actions to mitigate identified risks.
Web Application Testing
Web applications are crucial for business success and are prime targets for cybercriminals. Satius offers ethical hacking services, including penetration testing for websites and web applications, to pinpoint vulnerabilities such as SQL injection, cross-site scripting, and flaws in application logic and session management processes.
Cloud Penetration Testing
Cloud penetration testing presents complexities due to the unique rules of engagement set by each provider. Our tailored cloud security assessments assist your organization in navigating these challenges by identifying and resolving vulnerabilities that may jeopardize critical assets.
Wireless Testing
Unsecured wireless networks provide entry points for attackers to infiltrate your network and pilfer valuable data. Wireless penetration testing detects vulnerabilities, assesses potential damages, and outlines necessary remediation steps.
Social Engineering
Individuals remain a persistent vulnerability within organizational cybersecurity. Satius offers a social engineering penetration testing service, incorporating various email phishing scenarios to evaluate the capability of your systems and staff to identify and react to simulated attack simulations.
Mobile Security Testing
The utilization of mobile apps is increasing steadily, as companies increasingly offer customers access to their services through tablets and smartphones for added convenience. Satius conducts comprehensive evaluations of mobile applications, utilizing the latest development frameworks and security testing tools.
Why your organization needs a pen test
- Making significant changes to infrastructure
- Launching new products and services
- Undergoing a business merger or acquisition
- Preparing for compliance with security standards
- Bidding for large commercial contracts
- Utilising and/or developing custom applications
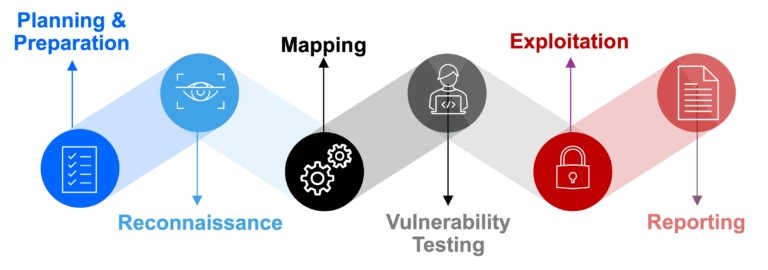
Our penetration testing process
Satius’s security penetration testing services are based on a systematic approach to vulnerability identification and reporting. Our advanced pentest methodology includes:
Common security vulnerabilities
By proactively identifying and exploiting vulnerabilities and providing clear help and advice to remediate issues, our ethical hacking and security penetration testing services enable you to understand and significantly reduce your organization’s cyber security risk.
Reporting you can trust
We won’t leave you hanging with just a list of vulnerabilities. Here’s what you can expect to receive post-assessment:
- A detailed outline of all risks identified
- The potential business impact of each issue
- Insight into ease of vulnerability exploitation
- Actionable remediation guidance
- Strategic security recommendations
Our award-winning security services
Satius’s security services are designed to provide the vital assistance needed to make tangible improvements to your organization’s cyber security posture.
Ready for Cyber Resilience?
Learn more how our Managed Service can help you achieve Cyber Resilience and be an extension of your team without breaking the budget.

TESTIMONIALS
What our clients say about us

Basheer Altayeb
We have been working with Satius for years to understand and minimize risks. The team performed multiple projects from vulnerability management to security controls validation. very satisfied with the value received.

Tedd Long
Partnering with Satius Security has been a game-changer for our organization. Their expert team and proactive approach have provided us with unmatched peace of mind in today's cyber landscape.

Steve Jablonski
Working with Satius Security has been instrumental in bolstering our company's cybersecurity defenses. Their proactive solutions and round-the-clock support have significantly enhanced our resilience against cyber threats. I highly endorse their services to any IT team looking to elevate their security posture.

Elie Hamouche
Satius is a professional IT Security Company that always gives the best value. We benefited from their recommendations and expertise to mitigate findings.
We work with organisations across a range of industries
- Finance
- Government
- Retail
- Healthcare
- Education
- Industrial