On Demand Assessments
PHISHING ATTACK SIMULATION
Enhance your Cyber Resilience against threats by reducing your people's exposure with phishing attack simulation.
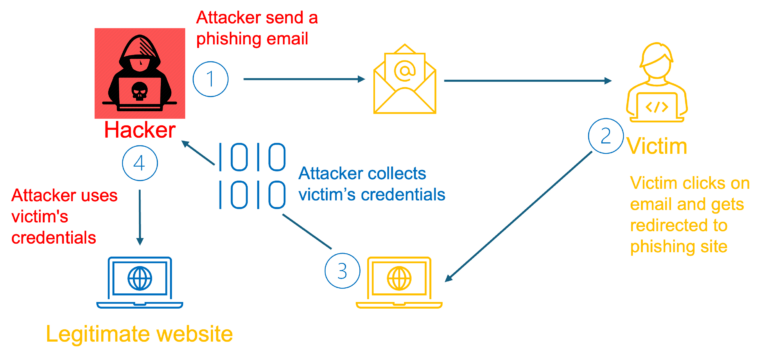
Phishing Attack Simulation mimics genuine phishing emails that organizations can send to employees to evaluate online behavior and gauge knowledge levels concerning phishing attacks. These emails replicate cyber threats professionals may encounter in their daily routines, both within and outside of work hours.
What Types of Phishing Simulation we cover?
Of the hundreds of the known phishing scams that exist, here are the four most common types we cover:
In email phishing attacks, urgency is a key tactic. Scammers distribute convincing emails to numerous recipients, urging them to change passwords or update personal and account information.
Smishing
This phishing method closely mimics email-based phishing. Hackers attempt to obtain confidential information from individuals by sending text messages that demand a response or additional action.
Spear Phishing
This strategy involves utilizing emails to launch targeted attack to a specific individual or organization. The perpetrator gathers personal details about their target and employs them to craft a customized and credible email.
CEO Fraud
Cyber criminals send emails pretending to be a C-level executive or simply a colleague, usually requesting a fund transfer or tax information.
PHISHING ATTACK SIMULATION PROCESS
Our Phishing Simulation Methodology
Satius Security attempts to build and execute a Phishing Simulation as realistically as possible to real attacks by mimicking the same process a real attacker takes. From reconnaissance phase to launching the campaign.
01
Reconnaissance
During this stage, we thoroughly examine your organization's online footprint to pinpoint potential vulnerabilities. By scrutinizing publicly accessible data and online behaviors, we acquire a deep understanding of your weak points. This enables us to customize our phishing simulations to replicate genuine threats, effectively testing your defenses and offering practical insights to enhance your cybersecurity posture.
02
Design scenarios
We initiate our design process by assessing your organization's environment. Subsequently, we develop customized phishing scenarios that replicate real-world attacks. Through the creation of persuasive emails, spoofed websites, and the application of social engineering tactics, we simulate authentic threats. This iterative method guarantees ongoing enhancement through feedback and the identification of emerging threats, bolstering your organization's ability to withstand cyber attacks.
03
Execute campaign
During this stage, we implement carefully orchestrated phishing campaigns utilizing sophisticated tools and methodologies. We distribute simulated phishing emails to your employees, closely monitoring their reactions and engagements.
Our focus is on realism and effectiveness. Through strategic timing and coordination, we aim to maximize employee engagement, providing valuable insights into your organization's ability to detect and respond to phishing attempts.
04
Report results
During the reporting phase, we examine the data gathered throughout the campaign to furnish actionable insights. This includes delivering a thorough summary of essential metrics such as click rates, response rates, and areas of vulnerability.
These insights enable you to understand the effectiveness of your organization's current security measures and identify areas for improvement.





