Managed Security Service
Ransomware Resilience as a Service
Shift to Ransomware Resiliency
Organizations of all sizes and across industries continue to be challenged with managing the risk and impacts of ransomware attacks. Developing a methodical approach to strategize, plan, prevent, detect, respond, recover, and report ransomware attacks is critical to effectively mitigate the inherent risks and impacts posed by ransomware. One of the greatest challenges ransomware attacks present is the wide range of possible attackers because the attacker can be anyone using any of the many different attack vectors.
Satius Security’s approach ensures the organization’s Technology, Process, and People’s readiness and capacity to disrupt the attack kill chain at every stage.

Benefits of Satius Security's Ransomware Resilience as a Service
Satius Security’s approach ensures the organization’s Technology, Process, and People’s readiness and capacity to disrupt the attack kill chain at every stage.
Reduce the likelihood and impact of an attack
Satius’s continuous journey to achieve and maintain the desired resilience maturity reduces threat exposure and the negative outcome of possible attacks.
Enhance your security posture and reputation
Our proactive and continuous assessment of exposure caused by shortcomings in security controls and misconfigurations along with people and process, leads to better security posture.
Comply with regulatory requirements
Satius RRaaS elevates your security capabilities to a level needed to help meet the requirements of the GDPR, NIS Directive, PCI DSS, ISO 27001, and more.
Save time and money on recovery and remediation
By having all processes related to threat’s protection, detection, and recovery assessed and updated, we insure optimal RTO and RTP.
Improve operational efficiency
Operating as an extension of your organization, Satius helps to make processes more efficient and enables you to quickly elevate security capabilities to enterprise level.
Expert guidance
Realize the value from assessments and guidance from Satius’s expertise in offensive security and adversarial mindset.
OVERVIEW
What is Ransomware?
Ransomware is a type of malware that locks and encrypts a victim’s data, files, devices or systems, rendering them inaccessible and unusable until the attacker receives a ransom payment. Attacks have evolved to target backups and exfiltrate data to be leveraged for double extortions and sold on the dark web.
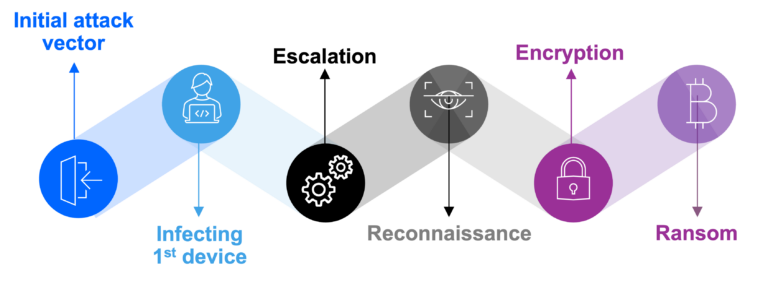
How Ransomware works?
Although ransomware methods and tactics have grown increasingly sophisticated in recent years, the typical attack still follows a consistent series of steps:
- Malware distribution and infection.
- Command and control.
- Discovery and lateral movement.
- File encryption and data theft.
- Extorsion.

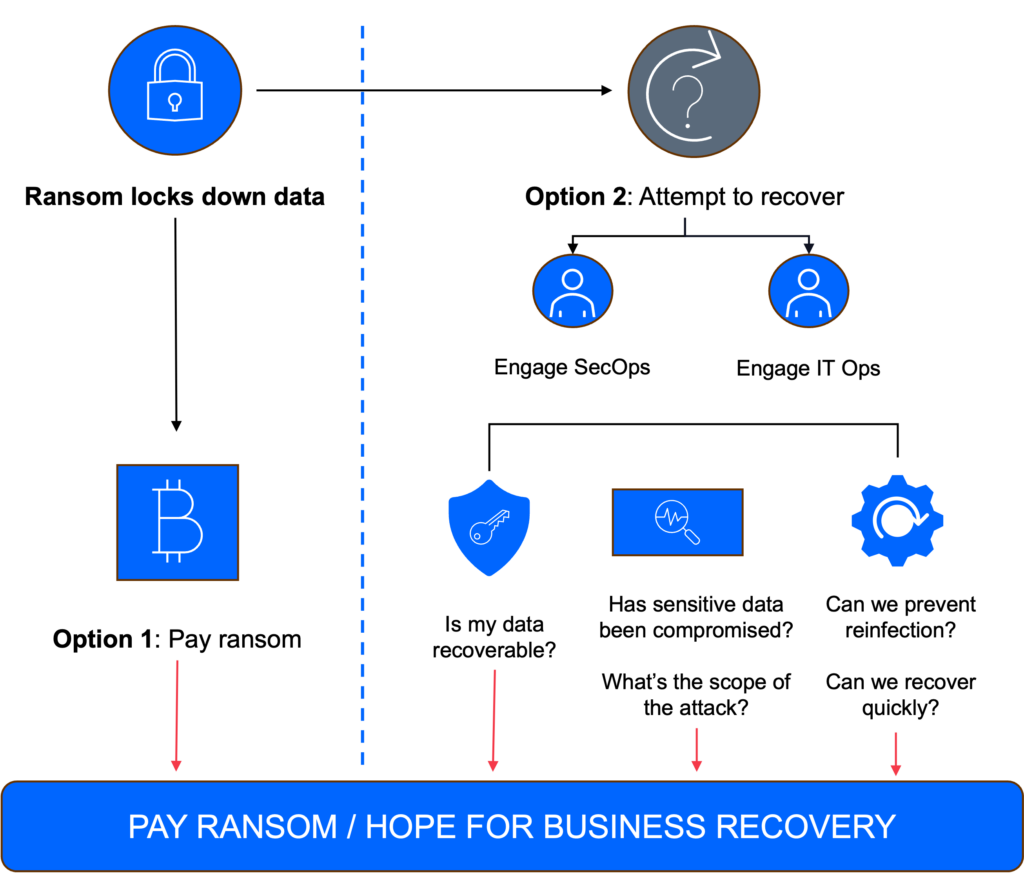
Don't get stuck paying for ransom
Mark Harris, Senior Director Analyst, Gartner
PROPERLY DETERMINE YOUR RPO AND RTO
When companies fail to determine their RPO (Recovery Point Objective) and RTO (Recovery Time Objective) properly, some feel as if they have no other choice but to pay the ransom. Yet, preparing and bypassing such attacks is not impossible. All of these issues can be resolved with specific and detail-oriented action plans in place for how to handle such emergencies.
BACKUPS DON’T ALWAYS WORK
Every organization should include backup as part of their ransomware response. It should not, however, be the sole component of that response. Backup is the recovery point of last resort. It is what you turn to when everything else has gone wrong. The right infrastructure software solution can ensure that “everything going wrong” is rare. Backups can’s be solely depended on for the following examples:
- Corrupt
- Infected
- RPO and RTO don’t meet requirements
CYBER INSURANCE NOT THE ANSWER
The insurance industry recognizes the importance of this cyber risk, and most policies cover ransomware including ransom demand amounts. Also, many insurers, also cover costs required to respond to the ransomware event — including digital forensics, costs to restore and recover lost assets, and even lost income due to business interruption. However, relying on insurance to mitigate the risk of ransomware doesn’t work.
SOPHOS “Cyber Insurance Adoption: The Critical Role of Frontline Cyber Defense” study revealed that ransomware victims with standalone cyber insurance policies are almost four times more likely to pay the ransom to recover encrypted data than those without cyber coverage. 58% of organizations with a standalone cyber insurance policy and had data encrypted in a ransomware attack last year paid the ransom to get their data back. In comparison, 36% of those with cyber as part of a broader insurance policy paid the ransom and 15% of those without cyber insurance.
PAID THE RANSOM
Satius brings together a continuous program to build, improve, and maintain ransomware resilience
Satius Security offers CTEM as a managed service, providing a framework for ongoing assessments, guidance, and reporting to enhance your overall risk management and cyber resilience.
ASSESS & MEASURE RESILIENCE
Clear insight on where you stand with metrics & reports
We start with a complete assessment of your people, processes, and technology’s readiness for ransomware threat. The assessments will produce metrics and detailed reports to guide us during the process of building resilience maturity. Assessments include:
- Build ransomware risk scenario
Conduct Resilience Assessment.
Phishing Attack Simulation
BUILD & IMPROVE RESILIENCE
Close gaps, build, and improve resilience maturity
This engagement builds on the results obtained from the initial assessment and the gap analysis performed. the process with build the necessary capacity to Protect, Detect, Respond, and Recover from ransomware attack. This will include:
- Review attack vectors
- Identify countermeasures
- Review Security Incident Management Plan
Run Tabletop Test (IT)
Document Workflow and Run-book
Run Tabletop Test (Leadership)
Prioritize resilience initiatives
MAINTAIN RESILIENCE
Prevents drifting of people, processes, and technologies from your goals
Our Ransomware Resilience as a Service is a program aimed to maintain resilience through a continuous cycle of assessment, capacity building, and improvement.
- Process Change Management
- Continuous Controls Validation
Routine Phishing Simulation
Resilience as a service vs. security as usual
Satius Vs. Others - what's the difference?
Satius’s Ransomware Resilience as a service can help organizations build a baseline security infrastructure focused on ransomware threat by addressing the entire attack cycle from People, Process, and Technology perspectives. Other provides will tend to address this threat from a generalized approach covering some or even most mitigations from ad-hoc rather than a holistic and continuous approach.
WHY SATIUS?
Your trusted partner for Managed Security Services
- Expertise in security challenges
- Rated 9/10 for overall customer satisfaction
- Accredited engineers in offensive security
- An outcome-focused approach
- Red and blue team security expertise
- Technology agnostic
Ready for Cyber Resilience?
Learn more how our Managed Service can help you achieve Cyber Resilience and be an extension of your team without breaking the budget.

TESTIMONIALS
What our clients say about us

Basheer Altayeb
We have been working with Satius for years to understand and minimize risks. The team performed multiple projects from vulnerability management to security controls validation. very satisfied with the value received.

Tedd Long
Partnering with Satius Security has been a game-changer for our organization. Their expert team and proactive approach have provided us with unmatched peace of mind in today's cyber landscape.

Steve Jablonski
Working with Satius Security has been instrumental in bolstering our company's cybersecurity defenses. Their proactive solutions and round-the-clock support have significantly enhanced our resilience against cyber threats. I highly endorse their services to any IT team looking to elevate their security posture.

Elie Hamouche
Satius is a professional IT Security Company that always gives the best value. We benefited from their recommendations and expertise to mitigate findings.
We work with organisations across a range of industries
- Finance
- Government
- Retail
- Healthcare
- Education
- Industrial

