Cyber threats are evolving faster than ever, and traditional vulnerability management methods are struggling to keep up. Organizations need to elevate their cybersecurity with continuous threat management—a proactive approach that consistently evaluates risks, reduces vulnerabilities, and aligns security efforts with business objectives. Gone are the days of reactive defenses; the future lies in continuous, data-driven improvement.
The Evolution of Cybersecurity: Why CTEM?
Think of traditional vulnerability management as looking for cracks in the foundation of your digital infrastructure. It’s a necessary start, but it only scratches the surface. CTEM, on the other hand, doesn’t just identify the cracks; it assesses their potential to cause harm, simulates real-world scenarios to determine the likelihood of exploitation, and prioritizes mitigation based on business-critical risks.
As Gartner notes, CTEM is about operationalizing exposure management cycles to continuously evaluate and reduce your attack surface. This proactive, cyclical approach ensures that your organization is always one step ahead of the threats targeting your digital assets. Elevate Cybersecurity with Continuous Threat Management
Key Differences: VM vs. CTEM
Static Lists vs. Contextual Insights
Traditional vulnerability management generates long lists of vulnerabilities. CTEM adds context, evaluating vulnerabilities in terms of their exploitability and the potential business impact.Periodic Checks vs. Continuous Monitoring
Vulnerability management often happens at scheduled intervals. CTEM operates continuously, ensuring no blind spots develop as your digital environment evolves.Reactive Fixes vs. Proactive Prevention
Vulnerability management reacts to discovered issues. CTEM anticipates potential threats, leveraging real-world attack simulations to validate defenses before a breach occurs.
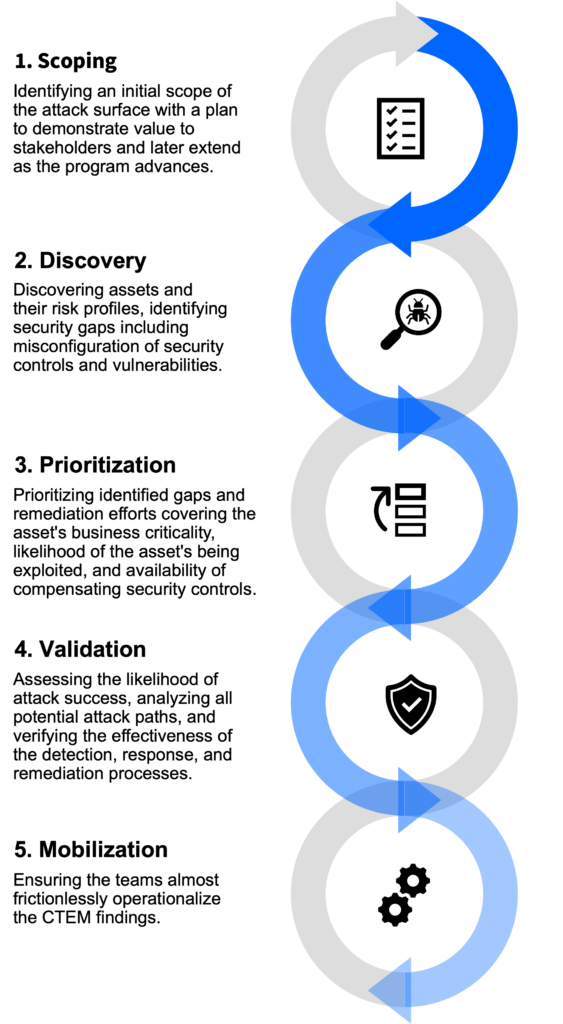
The Five Stages of CTEM
- Scoping: Define the attack surface, starting with the most critical assets and progressively broadening the scope.
- Discovery: Identify all assets and vulnerabilities, including misconfigurations and hidden risks.
- Validation: Simulate adversary tactics to test exploitability and measure your defense capabilities.
- Prioritization: Focus on gaps with the highest potential business impact and likelihood of exploitation.
- Mobilization: Operationalize findings, integrate them into workflows, and execute fixes.
Satius Security takes the Continuous Threat Exposure Management framework and transforms it into an operationalized service tailored to your organization’s unique needs. Here’s how we do it:
- Unified Threat Exposure Insight: A single-pane view of your entire security posture, complete with actionable risk assessments and visual dashboards like heat maps and trend analyses.
- Comprehensive Monitoring: 24/7 monitoring across your attack surface, covering endpoints, third-party risks, and cloud security.
- Real-World Simulations: Using breach and attack simulations, we validate vulnerabilities from an attacker’s perspective to reveal exploitable pathways.
- Business Alignment: Our solutions translate technical risks into business impacts, helping executives make informed decisions.
A Future-Ready Security Approach
By 2026, organizations leveraging CTEM will be three times less likely to suffer a breach compared to those relying solely on traditional methods. Don’t let your cybersecurity strategy fall behind. Elevate from mere vulnerability management to a proactive, robust defense system that continuously strengthens your cyber resilience.
Ready to Elevate Cybersecurity with Continuous Threat Management
Satius Security’s CTEM as a Service is your partner in operationalizing threat exposure management. From ongoing assessments to actionable reporting, we empower your organization to stay one step ahead of evolving cyber threats.