Managed Security Service
CONTINUOUS THREAT EXPOSURE MANAGEMENT as a service
Gain Comprehensive Insights into Your Security Posture with Clear, Actionable Risk Assessments.
Elevate Your Cyber Defense: Transition from Traditional Vulnerability Management to Proactive Risk Management
How to Manage Cybersecurity Threats, Not Episodes
By 2026, organizations that prioritize their security investments based on a continuous exposure management program will be 3x less likely to suffer a breach.
Gartner
why SATIUS'S continuous threat exposure management as a service?
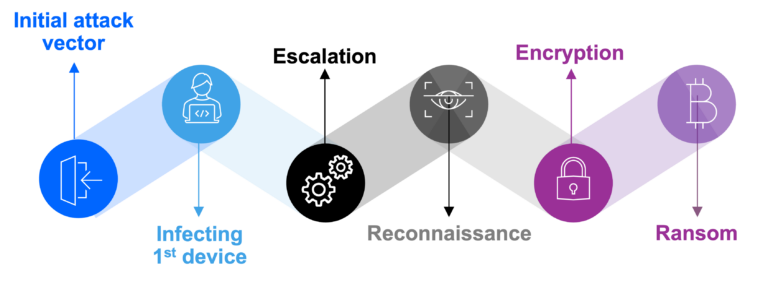
Amid escalating cyber threats, adopting a proactive strategy is essential.
Our Threat Exposure Management as a Service offers continuous monitoring, threat validation, and tailored security enhancements, utilizing industry-standard frameworks. We present results in clear letter grades, scores, and indices, providing quantifiable measures of threat category management and overall threat mitigation.
-
Reduce Risk Exposure
Leverage real-world attack simulations to identify and mitigate vulnerabilities, minimizing potential threats.
-
Comprehensive Monitoring
Oversee your attack surface across 20 technical categories, ensuring no vulnerability goes unnoticed.
-
Optimize Security Investments
Utilize risk quantification to comprehend the financial implications of potential threats, enabling informed investment decisions.
-
Ensure Compliance
Achieve and maintain compliance with industry standards and regulations, safeguarding your organization's reputation.
ctem actionable insight
Streamlined, Continuous Protection for Peace of Mind
Satius Security offers CTEM as a managed service. Therefore, providing a framework for ongoing assessments, guidance, and reporting to enhance your overall risk management and cyber resilience.


A holistic approach proceeds from an accurate overview of the risk landscape—a governing principle that first of all requires accurate risk reporting. The goal is to empower organizations to focus their defenses on the most likely and most threatening cyber risk scenarios, achieving a balance between effective resilience and efficient operations.
Executive Management needs Holistic strategy to cyber risk
Companies are rolling out a wide range of activities to counter cyber risk. They are investing in capability building, new roles, external advisers, and control systems. What they lack, however, is an effective, integrated approach to cyber risk management and reporting.
McKinsey & Company

A holistic approach proceeds from an accurate overview of the risk landscape—a governing principle that first of all requires accurate risk reporting. The goal is to empower organizations to focus their defenses on the most likely and most threatening cyber risk scenarios, achieving a balance between effective resilience and efficient operations. Tight controls are applied only to the most crucial assets. The holistic approach lays out a path to root-cause mitigation in four phases.
Cyber risk is now as important a priority for the leaders of public and private institutions as financial and legal risks. Facing a rising threat level and the magnitude of the potential impact, executives are insisting on full transparency around cyber risk and effective ways to manage it actively.
CISOs: Elevate Your Cybersecurity Reporting to the Boardroom
Struggling to bridge the gap between technical cybersecurity metrics and what your board actually wants to see? You’re not alone.
Download our free guide:
“CISO’s Guide To Reporting Cyber Security”
That’s why we’ve created the “CISO’s Guide to Reporting Cyber Security“—a step-by-step resource to help you:
- Present cybersecurity insights in a language the board understands.
- Align security metrics with business goals and priorities.
- Build trust and demonstrate ROI on your cybersecurity investments.
What is Continuous Threat Exposure Management Framework (CTEM)?
Experience Proactive Cyber Risk Management Today:
Satius Security brings the CTEM framework to life with ongoing assessments, expert guidance, and actionable reporting—empowering your organization to strengthen risk management and build cyber resilience.
Streamlined, Continuous Protection for Peace of Mind.
Satius Security operationalizes CTEM framework to provide an ongoing assessments, guidance, and reporting to enhance your overall risk management and cyber resilience.
Core Threat Exposure Management Components
Empower Your Security with Industry-Leading Validation and Monitoring
Our solution is offered in two ways to accommodate your needs and budget. Basic Proactive Threat Management Aligned with Established Security Frameworks such as FAIR and MITRE ATT&CK. Advanced to enhance Your Defense Strategy with Advanced Risk Management
Tailored for both executive and technical users, our dashboards transform complex data into actionable insights, empowering teams to drive Cyber Resilience and make informed decisions quickly.
Add Detection & Response and Cloud Security Posture assessments for a more comprehensive view of your security controls' effectiveness, with actionable recommendations for improvement.
Expand your threat exposure management
Tailored Add-Ons for Comprehensive Security Management
Customize Your Threat Management Solution to Fit Your Unique Needs with modular add-ons that address specific organizational requirements, enabling clients to build a complete security posture.
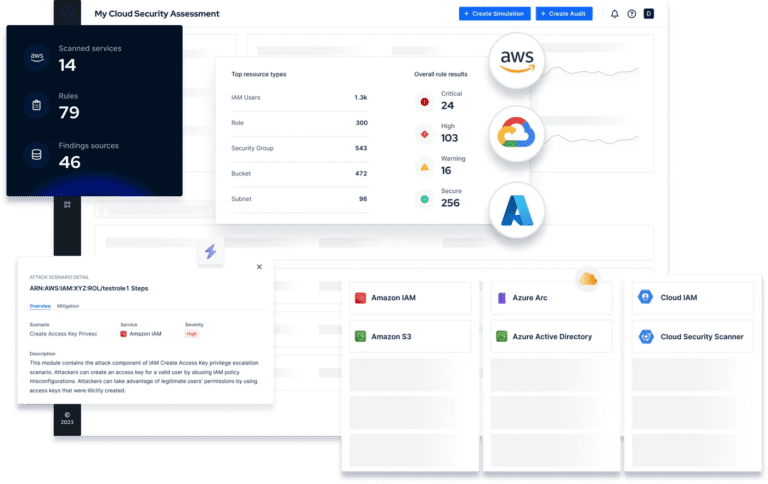
Satius Cloud Security Validation helps security teams keep pace with cloud security posture management by identifying common misconfigurations and overly permissive IAM policies – the two primary causes of cloud data breaches.
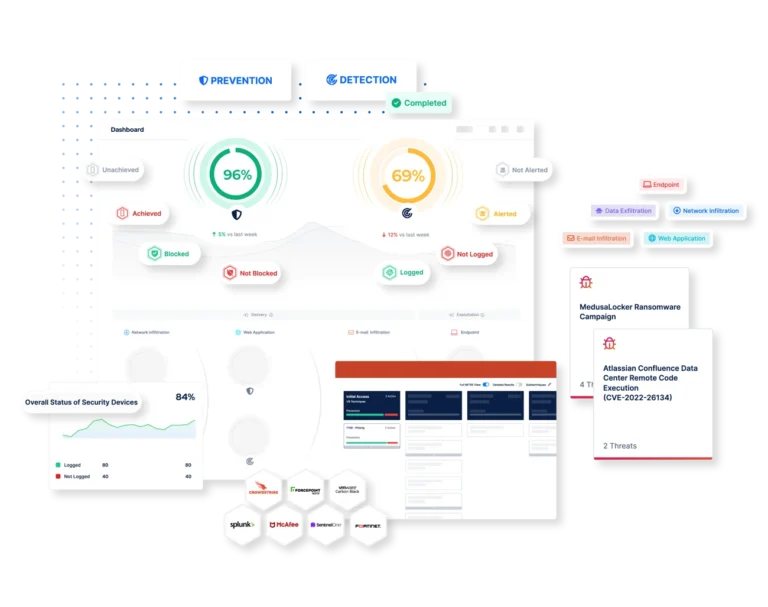
Boost Detection Effectiveness. Increase your detection capabilities. Get rid of false positives. Mitigate risks swiftly.
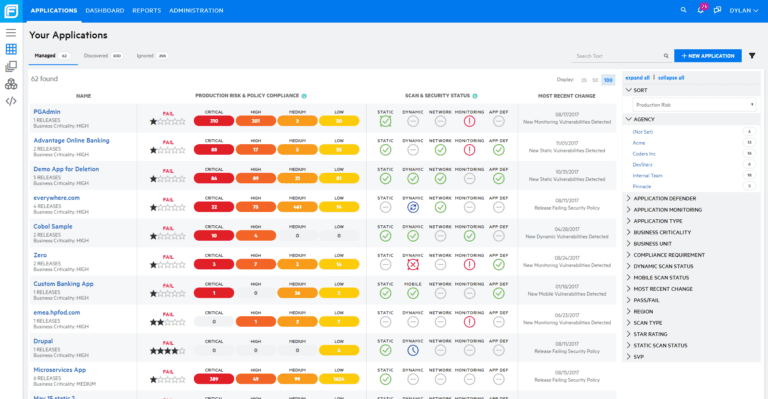
Enhance application resilience with Webinspect dynamic application security testing to identify and validate high risk security vulnerabilities in running applications.
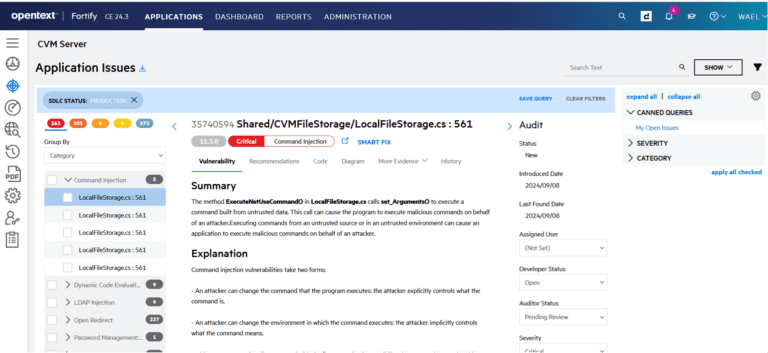
Leverage Static Code Analyzer for static application security testing (SAST) to build security into the development process. Static Code Analyzer pinpoints the root cause of the vulnerability, prioritizes results, and provides best practices so developers can code more securely.

Evaluate and manage risks posed by third-party vendors, utilizing contextual data to prioritize remediations.
Identify and remediate web application vulnerabilities before they can be exploited.
benefits of threat exposure management
Benefits of Satius Security's Threat Exposure Management as a Service
Satius Security offers TEM as a managed service. Therefore, providing a framework for ongoing assessments, guidance, and reporting to enhance your overall risk management and cyber resilience.
Reduced Breach Risk
Identify and mitigate vulnerabilities before they are exploited
Enhanced Compliance
Stay aligned with regulations like PCI DSS, HIPAA, and GDPR
Increased Efficiency
Free up your team to focus on high-priority tasks with automated monitoring
Reporting
Get the answers Executives need to provide directions with actionable insight reporting and defensible data to drive improvement and resiliency.
Exper-Led
The program is managed by certified expert cybersecurity engineers with the knowledge and expertise in all phases of the TEM program.
Adaptable Add-Ons
Tailor your security strategy to address your organization’s specific needs
DISCOVER HOW SATIUS CAN DRIVE YOUR CYBER RESILIENCE
TESTIMONIALS
What our clients say about us

Tedd Long
Partnering with Satius Security has been a game-changer for our organization. Their expert team and proactive approach have provided us with unmatched peace of mind in today's cyber landscape.

Steve Jablonski
Working with Satius Security has been instrumental in bolstering our company's cybersecurity defenses. Their proactive solutions and round-the-clock support have significantly enhanced our resilience against cyber threats. I highly endorse their services to any IT team looking to elevate their security posture.

Elie Hamouche
Satius is a professional IT Security Company that always gives the best value. We benefited from their recommendations and expertise to mitigate findings.

Basheer Altayeb
We have been working with Satius for years to understand and minimize risks. The team performed multiple projects from vulnerability management to security controls validation. very satisfied with the value received.
We work with organisations across a range of industries
- Finance
- Government
- Retail
- Healthcare
- Education
- Industrial

