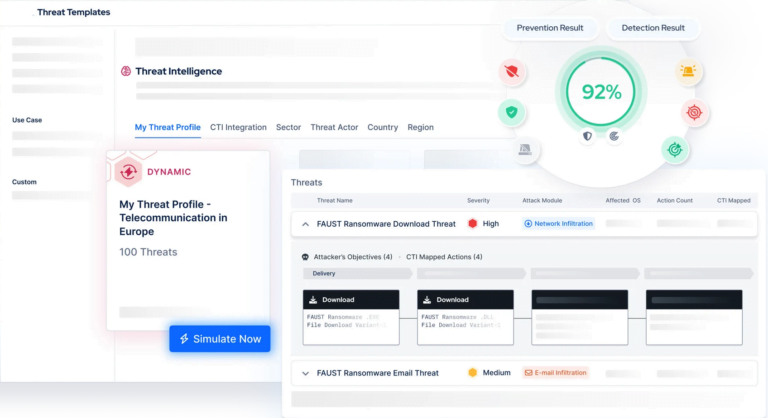
On Demand Assessments
Scenario Based Security Testing
Mimic real-word attacks from vectors which are most relevant to the business in question.
Organizations of all sizes and across industries continue to be challenged with managing the risk and impacts of ransomware attacks. Developing a methodical approach to strategize, plan, prevent, detect, respond, recover, and report ransomware attacks is critical to effectively mitigate the inherent risks and impacts posed by ransomware. One of the greatest challenges ransomware attacks present is the wide range of possible attackers because the attacker can be anyone using any of the many different attack vectors.
Satius Security’s approach ensures the organization’s Technology, Process, and People’s readiness and capacity to disrupt the attack kill chain at every stage.
OVERVIEW
Real-life assessments to evaluate prevention, detection and response capabilities
Relying solely on efficiency metrics to gauge the success of security operations may overlook a crucial question that all security leaders must address: How effective are people and controls in thwarting, detecting, and responding to cyber threats?
Through scenario-based testing conducted by Satius’s seasoned team of consultants, organizations can validate the genuine efficacy of their capabilities. This entails simulating a diverse array of adversarial tactics and offering recommendations to fortify the protection of critical assets.

Our security qualifications
Our experts hold numerous industry certifications and vendor specific certified trainings to insure standardized approach and optimal results.
Benefits of scenario-based testing
BENEFITS
Scenario-based testing represents a specialized variant of offensive security assessment. Unlike conventional penetration testing, which concentrates on revealing vulnerabilities, scenario-based testing aims to evaluate the effectiveness of cybersecurity controls against particular adversarial tactics and behaviors. It aids in addressing crucial inquiries such as:
- How effective are security technologies at preventing, detecting and responding to threats?
- Are there any network security blind spots that persistent attackers could exploit?
- How good are security analysts at differentiating genuine incidents from false positives?
- Are Blue Team security analysts able to shut down advanced and sophisticated attacks?
- Do in-house security teams have the know-how to remediate breaches?
- Are incident response plans in place to address threats and manage compromises?
PURPOSE
Validate the effectiveness of security operations
Scenario-based testing serves as a prevalent method to evaluate your organization’s capability in preventing, detecting, and responding to threats. Unlike a Red Team Operation, which replicates a comprehensive cyber-attack, scenario-based testing is a more targeted assessment typically centered on a specific adversarial tactic. Consistent scenario-based testing fosters a culture of ongoing enhancement, equipping your security operations team to effectively combat current and emerging threats.
Assessment
Custom assessments
Satius Security’s scenario-based testing service can be tailored to help evaluate your organization’s ability to detect and respond to a range of security risks. The many scenarios and tactics that we can replicate include:
- A supply chain compromise
- Installation of malware
- Data exfiltration by an employee or contractor
- A spear phishing campaign to harvest credentials
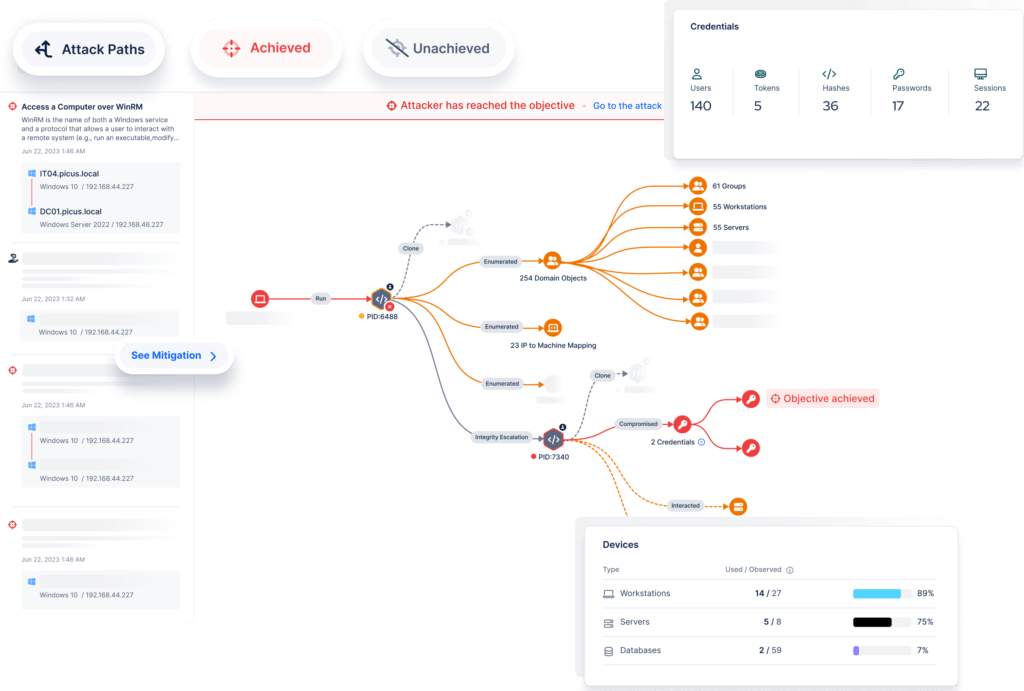
our framework
The MITRE ATT&CK™ framework
Scenario-based testing can be aligned to a range of adversarial behavior frameworks. One of the most common is the Adversarial Tactics, Techniques and Common Knowledge (MITRE ATT&CK), which outlines the methods adversaries use to compromise, exploit and traverse networks. The MITRE ATT&CK Framework is divided into 11 groups of TTPs, all of which can be replicated by scenario-based testing.
01
Initial Access
Gaining a foothold in the target network using tactics such as spear phishing and supply chain compromise.