As organizations increasingly rely on third-party providers to manage Endpoint Detection and Response (EDR) or Managed Detection and Response (MDR) solutions, ensuring these services are performing optimally becomes a critical component of maintaining a robust cybersecurity posture. Breach and Attack Simulation (BAS), paired with the MITRE ATT&CK framework, offers a powerful method to validate the effectiveness of third-party-managed endpoint security solutions.
The Challenge: Trust but Verify
Third-party EDR/MDR services are designed to detect, prevent, and respond to threats on behalf of the organization. However:
Visibility Gap: Organizations often lack direct insight into how well their EDR/MDR providers are addressing specific threats.
- Dynamic Threat Landscape: The tactics, techniques, and procedures (TTPs) used by attackers evolve rapidly, challenging even the most skilled providers.
- Accountability and SLA Validation: Businesses need to ensure that providers are meeting Service Level Agreements (SLAs) for threat detection and response.
Breach and Attack Simulation addresses these challenges by providing a measurable, repeatable, and transparent process to assess the real-world efficacy of endpoint security management.
The Use Case: Leveraging BAS for 3rd-Party Validation
Scenario:
A financial services organization partners with a leading MDR provider to manage their endpoint security. While the provider delivers regular reports and updates, the organization seeks an independent assessment to verify the MDR’s ability to detect and respond to advanced attack techniques.
Approach:
- Framework Alignment: The organization uses BAS tools mapped to the MITRE ATT&CK framework, ensuring simulations align with known adversarial techniques and tactics.
- Library of Real-World Attacks: The BAS platform executes a range of simulations, including ransomware attacks, credential theft, lateral movement, and data exfiltration, mirroring real-world scenarios.
- Continuous Testing: The organization schedules regular simulations to test the MDR’s capabilities in different conditions, ensuring consistent performance over time.
Outcomes:
Validation of Detection Capabilities:
- The BAS simulation reveals how well the MDR identifies and responds to attack behaviors such as credential harvesting or privilege escalation.
- Any detection gaps, such as missed techniques or slow response times, are highlighted.
Accountability and SLA Alignment:
- Results from the BAS are benchmarked against the SLAs agreed upon with the MDR provider. For example, a requirement to detect and respond to ransomware within a set timeframe can be directly tested and validated.
Improved Incident Response:
- Simulations highlight areas where response times or processes could be optimized, providing actionable insights for the MDR team to enhance their services.
Enhanced Reporting and Communication:
- The BAS platform provides clear, quantifiable results (e.g., heat maps, risk scores, and detection timelines), bridging the communication gap between technical teams and executive stakeholders.
Continuous Improvement:
- The MDR provider uses feedback from the BAS tests to adjust configurations, refine detection rules, and enhance their overall service offering.
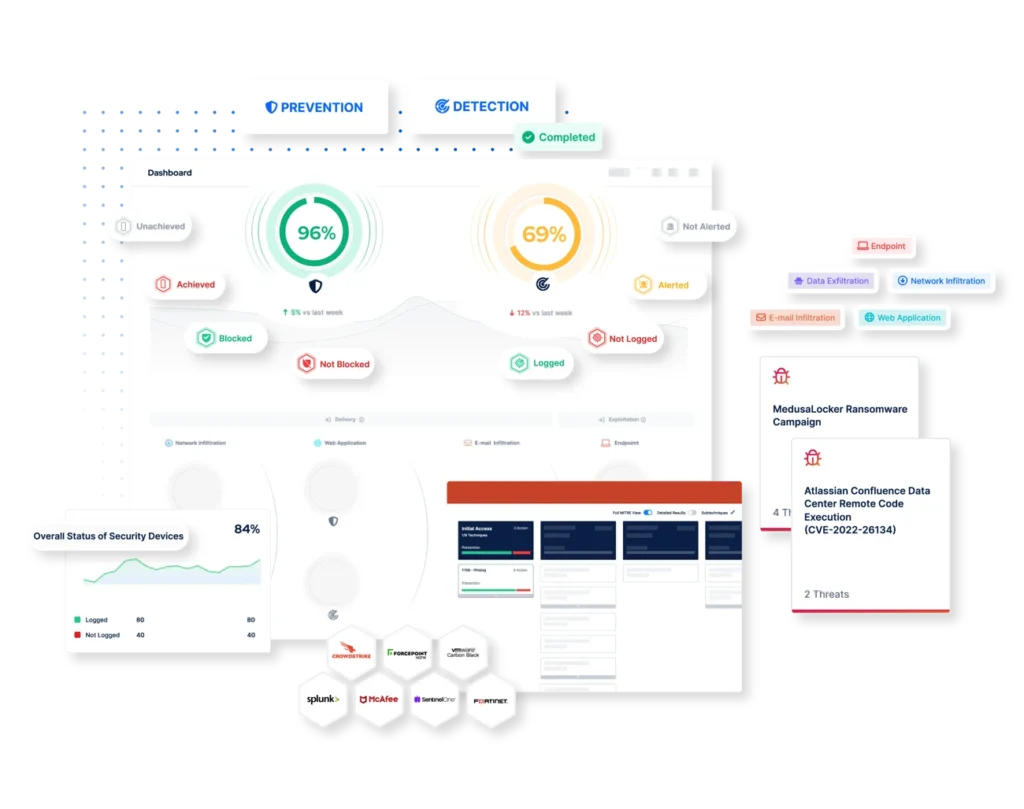
The Power of MITRE ATT&CK and BAS
The MITRE ATT&CK framework is integral to this process, offering:
- Comprehensive Coverage: Mapping simulated attacks to a globally recognized framework ensures that the assessment covers a broad spectrum of potential threats.
- Standardized Metrics: The results can be compared across providers or internal teams, enabling objective performance evaluation.
- Proactive Defense: Testing against the latest TTPs prepares organizations to handle emerging threats effectively.
Conclusion: Empowering Confidence in Third-Party Security
For organizations relying on third-party EDR/MDR providers, Breach and Attack Simulation combined with the MITRE ATT&CK framework offers an invaluable tool for ensuring these services meet their promises. This proactive validation approach not only identifies gaps but also builds a culture of accountability, ensuring that the partnership with the provider delivers robust and effective endpoint security.
By regularly testing and validating the performance of third-party-managed security solutions, businesses can gain confidence that their defenses are not just functional but prepared to handle the dynamic and evolving threat landscape.
Ready for Cyber Resilience?
Learn more how our Assessments and Managed Service can help you validate the effectiveness of your Managed EDR (MDR) without breaking the budget.

