In the complex and ever-evolving world of cybersecurity, organizations face the daunting task of protecting their infrastructure against increasingly sophisticated threats. To address these challenges, leveraging the MITRE ATT&CK framework in conjunction with Breach and Attack Simulation (BAS) has become a leading approach to validating cybersecurity controls, particularly for endpoints and networks.
Understanding the MITRE ATT&CK Framework
The MITRE ATT&CK framework is a globally recognized knowledge base of adversarial tactics and techniques based on real-world observations. It provides a comprehensive matrix of behaviors used by threat actors during the lifecycle of an attack, helping organizations understand potential attack vectors and vulnerabilities within their environment.
Breach and Attack Simulation: The Game Changer
BAS tools enable continuous and automated testing of an organization’s security defenses by simulating real-world attack scenarios. These tools replicate various stages of an attack, from reconnaissance to exploitation, providing actionable insights into the effectiveness of security controls.
When integrated with the MITRE ATT&CK framework, BAS tools can:
Map Simulations to Known Techniques: Align simulated attacks with specific MITRE ATT&CK tactics and techniques to evaluate the robustness of an organization’s defenses.
- Identify Gaps in Controls: Highlight weaknesses in detection, response, and prevention measures across endpoints and network layers.
- Deliver Actionable Remediation Insights: Provide clear guidance for improving security controls.
Benefits of Operationalizing MITRE ATT&CK with BAS
Enhanced Control Validation:
- BAS tools test the efficacy of endpoint and network defenses against the latest adversarial techniques, validating detection rules, logging, and response protocols.
- This proactive approach ensures that configurations, rules, and threat intelligence are continuously fine-tuned to mitigate evolving risks.
Continuous Threat Exposure Management (CTEM):
- Aligning BAS with a CTEM approach enables organizations to prioritize vulnerabilities based on their criticality and threat likelihood.
- This helps allocate resources efficiently, addressing the most pressing security gaps while maintaining a holistic view of the organization’s threat landscape.
Improved Incident Response Readiness:
- By regularly simulating attack paths, organizations can measure the time it takes to detect and respond to breaches, identifying areas where incident response can be improved.
Compliance and Reporting:
- The integration of MITRE ATT&CK and BAS supports regulatory compliance by providing quantifiable data and clear reporting on security posture.
Use Case: Endpoint and Network Security Validation
Endpoints and networks form the backbone of any IT environment, making their security paramount:
- Endpoints: BAS tools simulate malware delivery, lateral movement, and persistence techniques to evaluate endpoint detection and response (EDR) capabilities.
- Networks: Simulations test intrusion detection systems (IDS), firewalls, and network segmentation by mimicking traffic patterns and lateral attack movements.
Conclusion
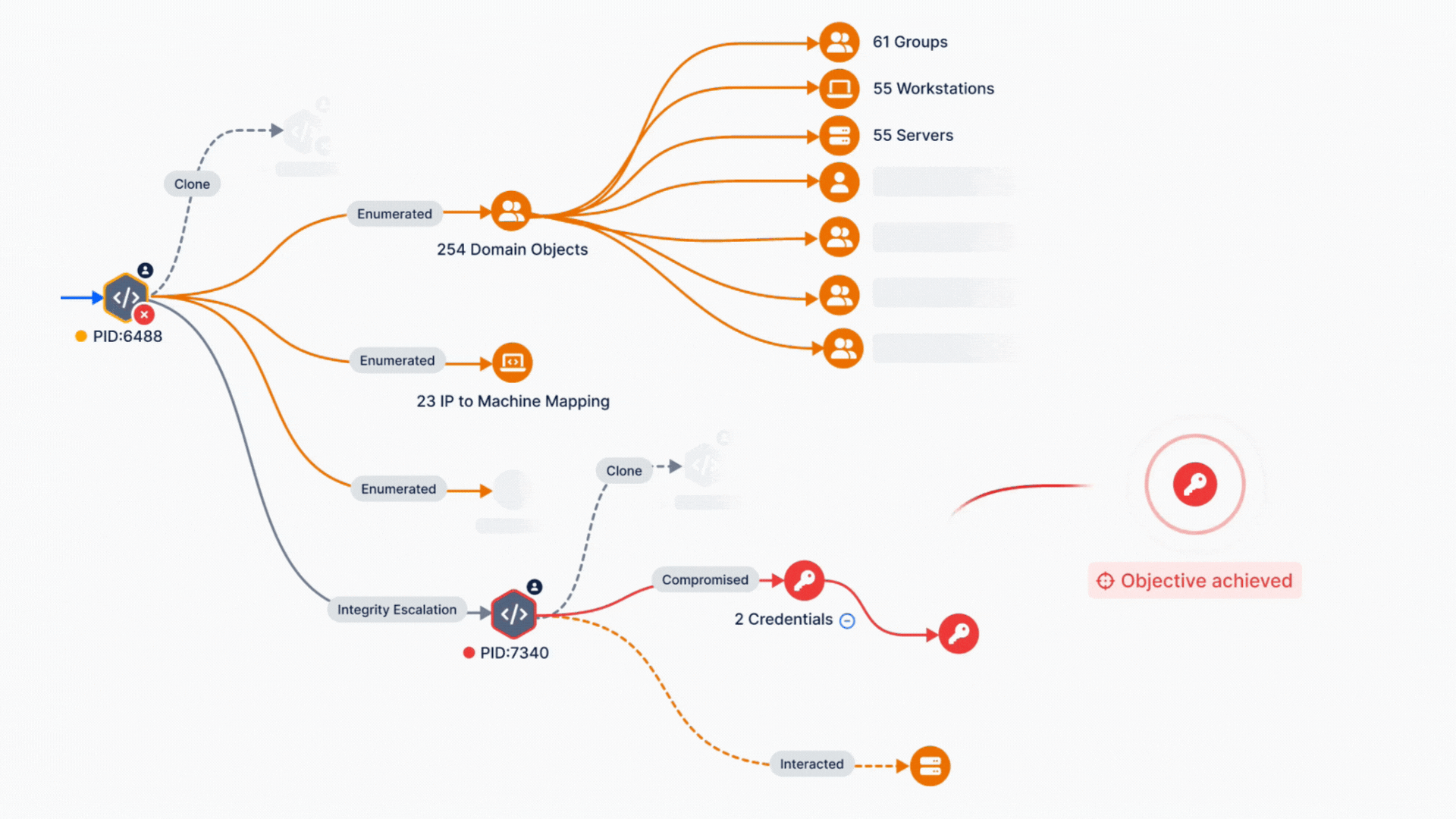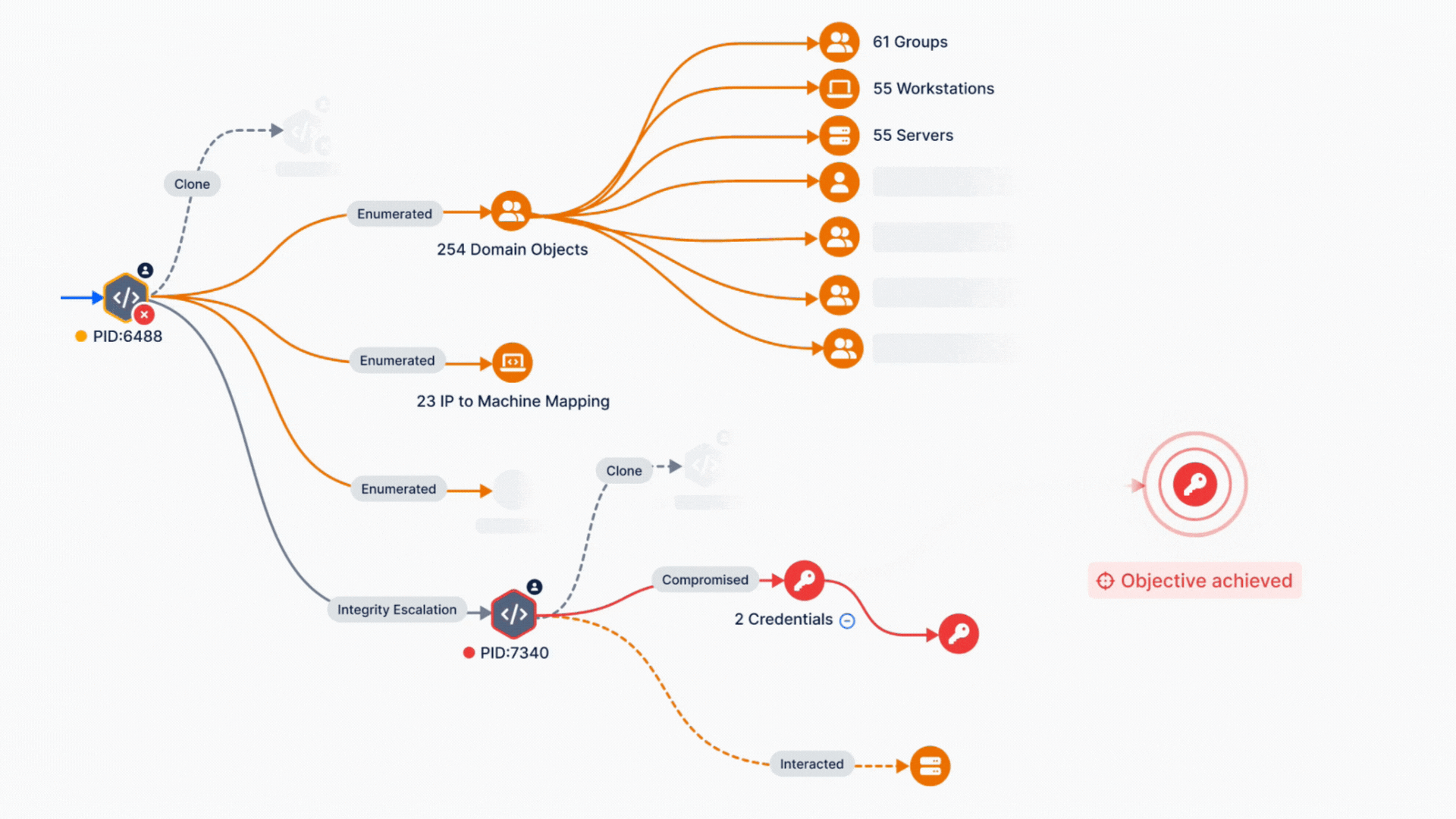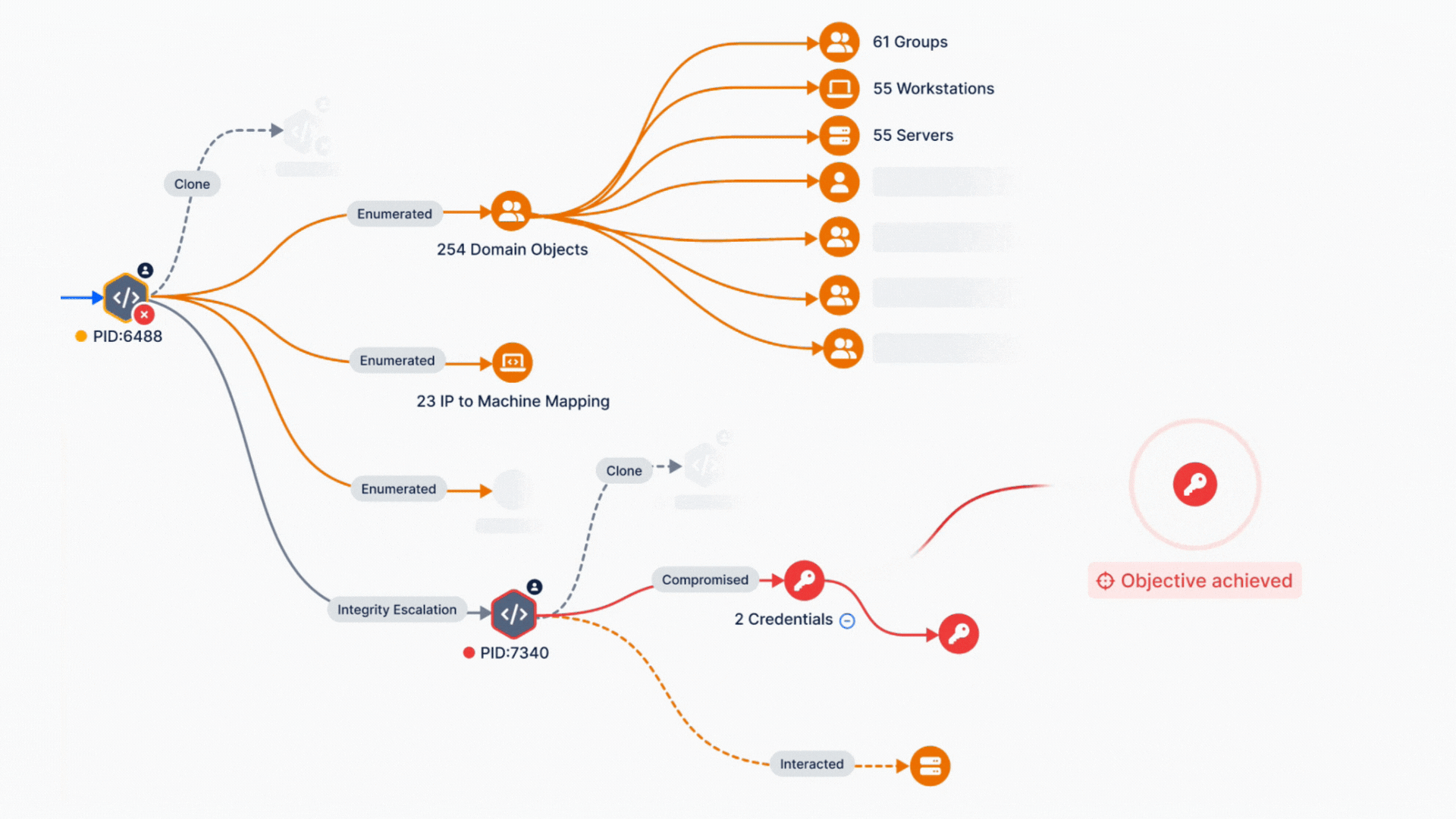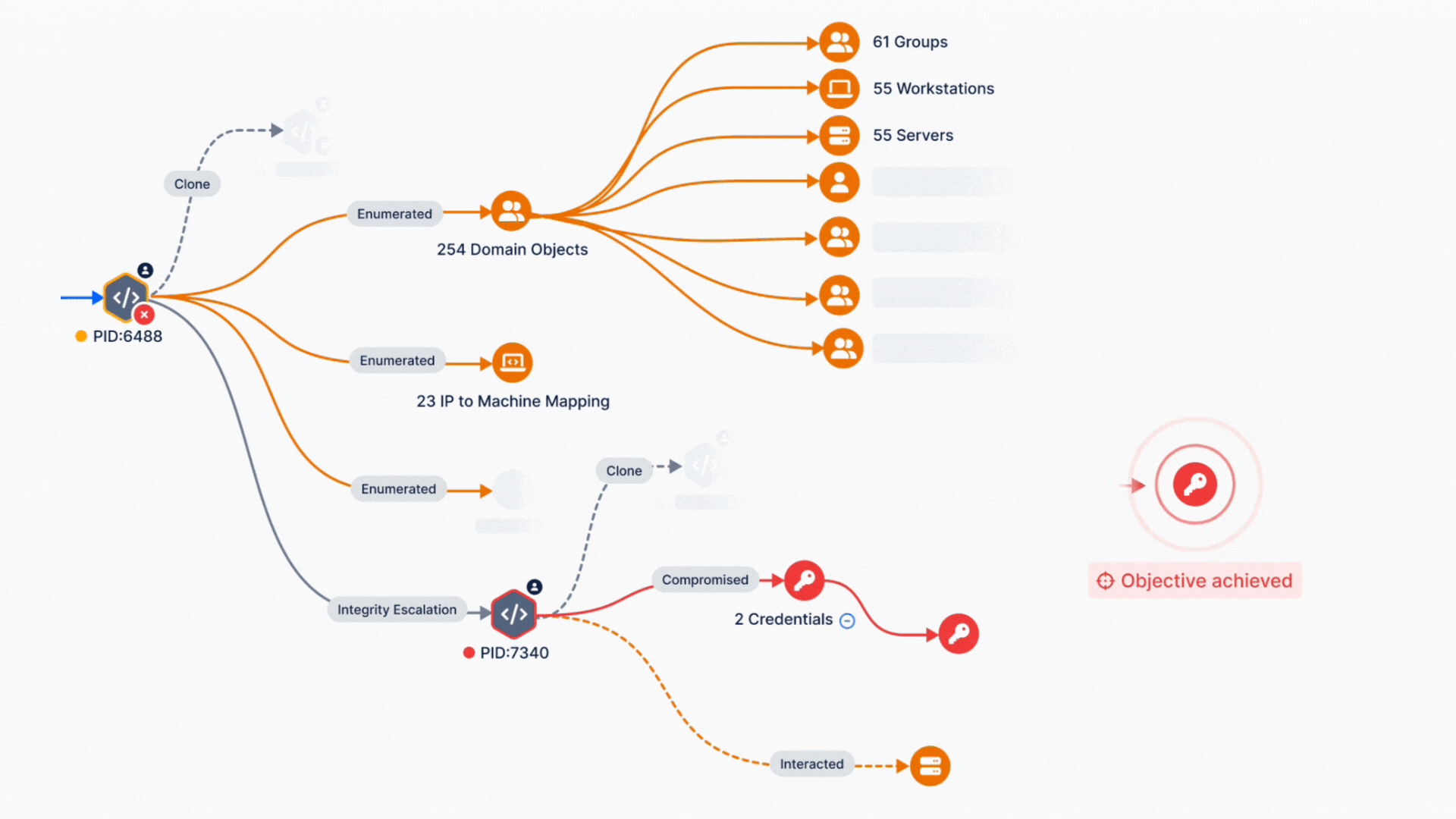
Operationalizing the MITRE ATT&CK framework with Breach and Attack Simulation is a game-changing strategy for validating and enhancing cybersecurity controls. By aligning real-world threat simulations with this detailed framework, organizations can transition from reactive to proactive defense, ensuring their endpoint and network defenses are not just functional but optimized for today’s threat landscape.
As cyber threats grow more complex, adopting such integrated approaches will empower organizations to not only mitigate risks but also build a resilient cybersecurity posture, ensuring long-term protection and business continuity.
Ready for Cyber Resilience?
Learn more how our Security Controls Validation Assessments and Managed Service can help you achieve Cyber Resilience without breaking the budget.

