When it comes to cybersecurity, one question keeps many decision-makers awake at night: Are we doing enough to protect our organization from threats? Knowing where your security controls stand in comparison to industry peers is critical, but it’s not always easy to gauge. That’s where security controls validation steps in, offering clarity in a complex landscape.
The Power of Security Controls Validation
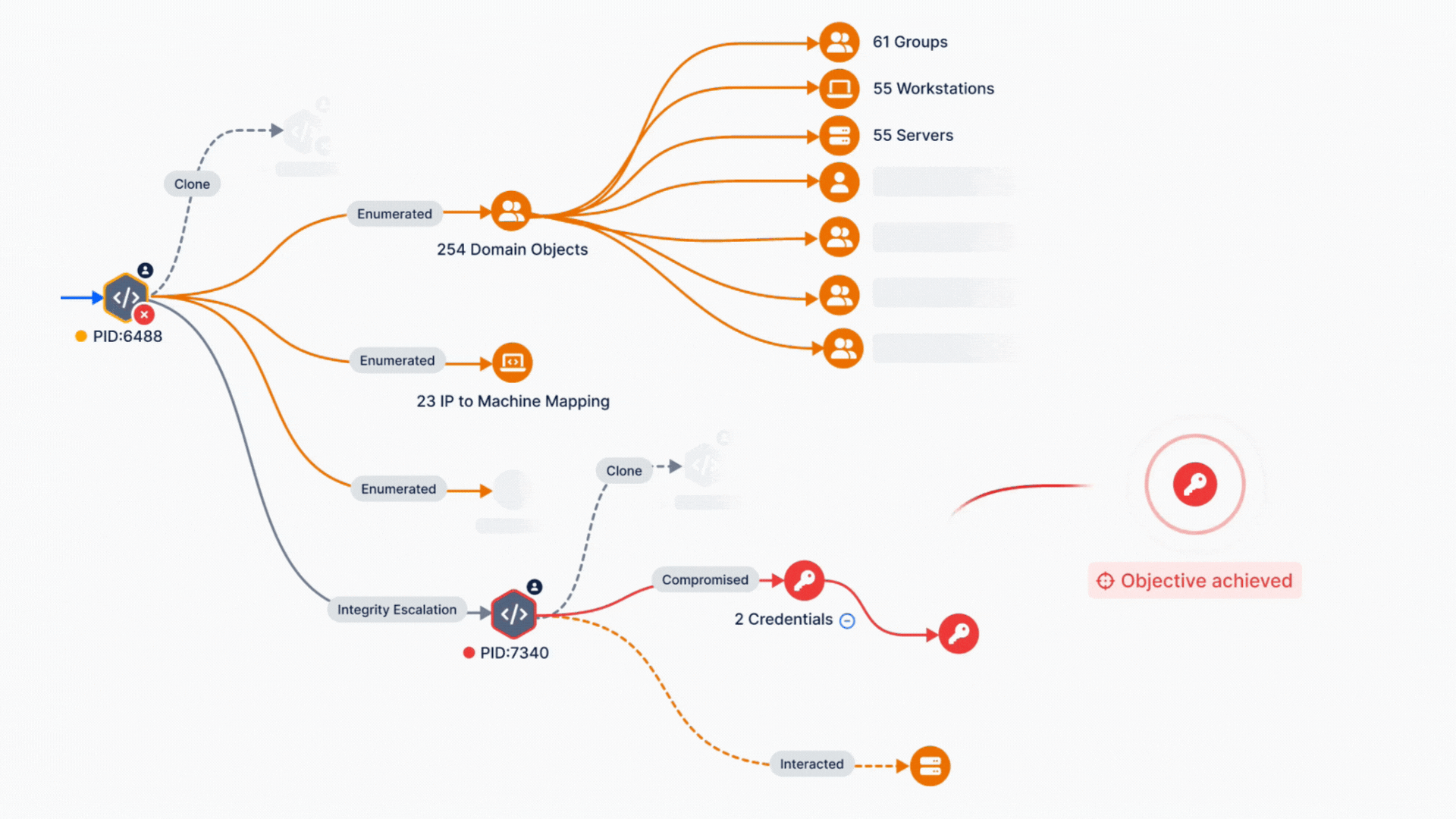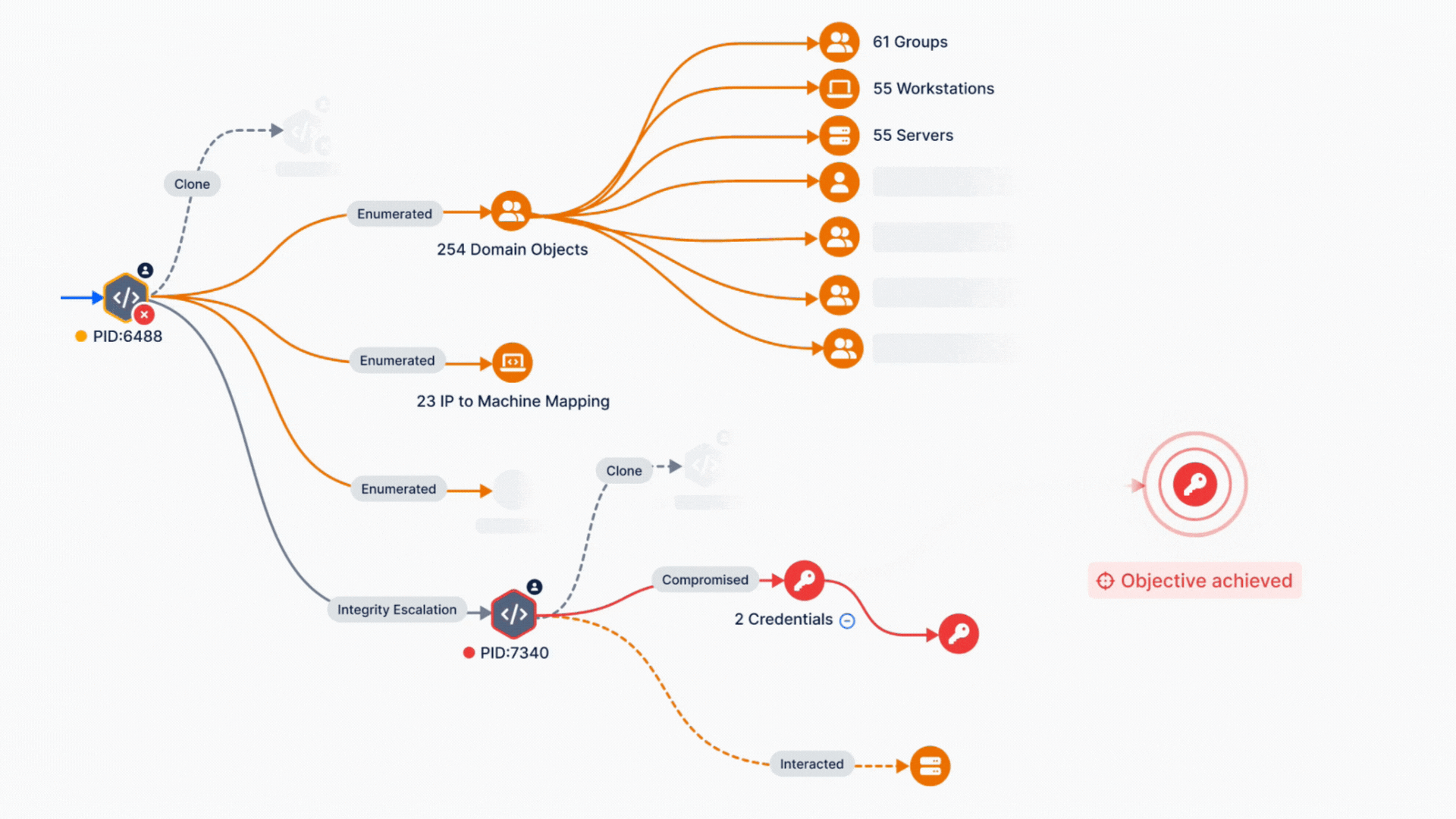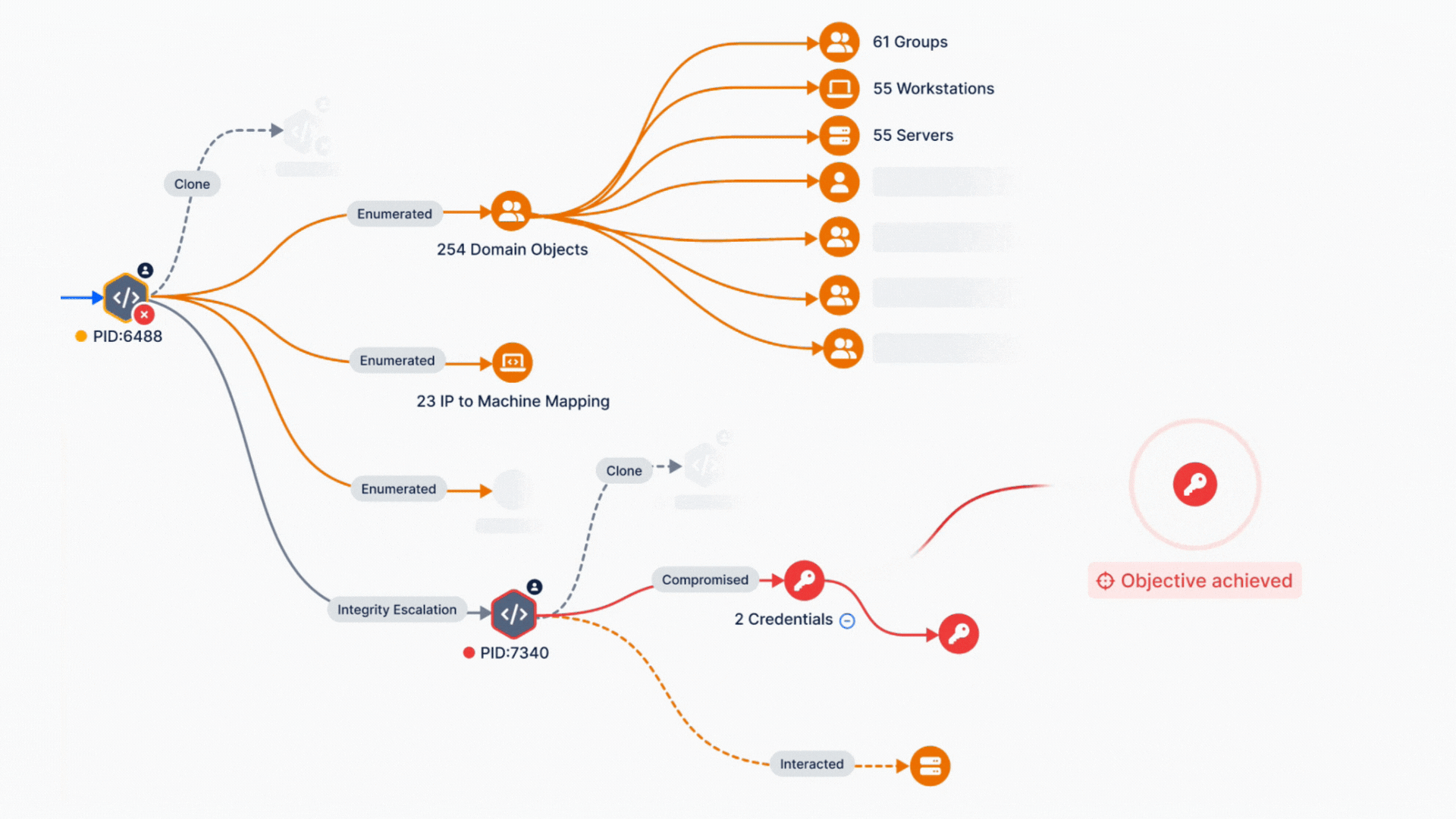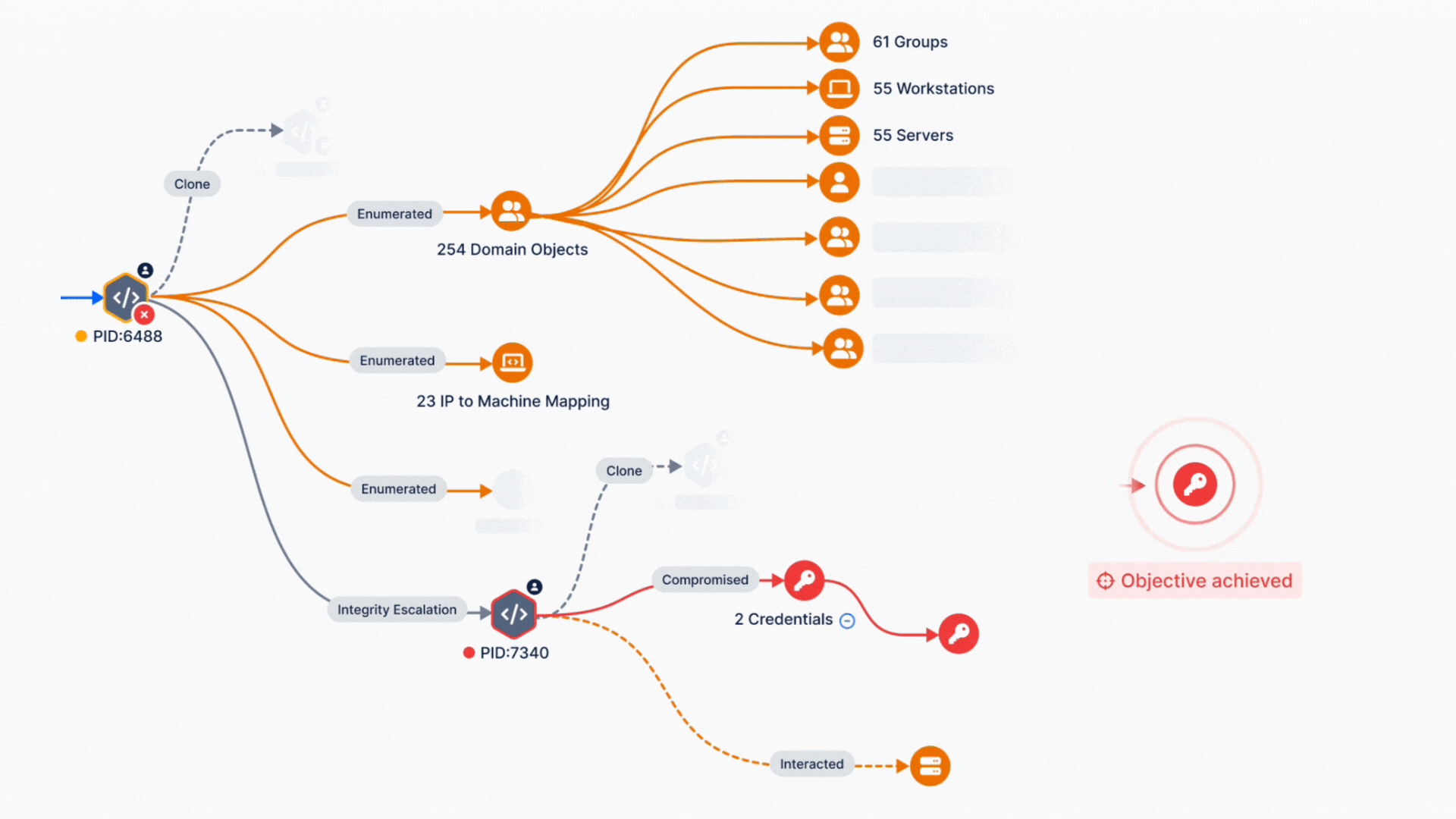
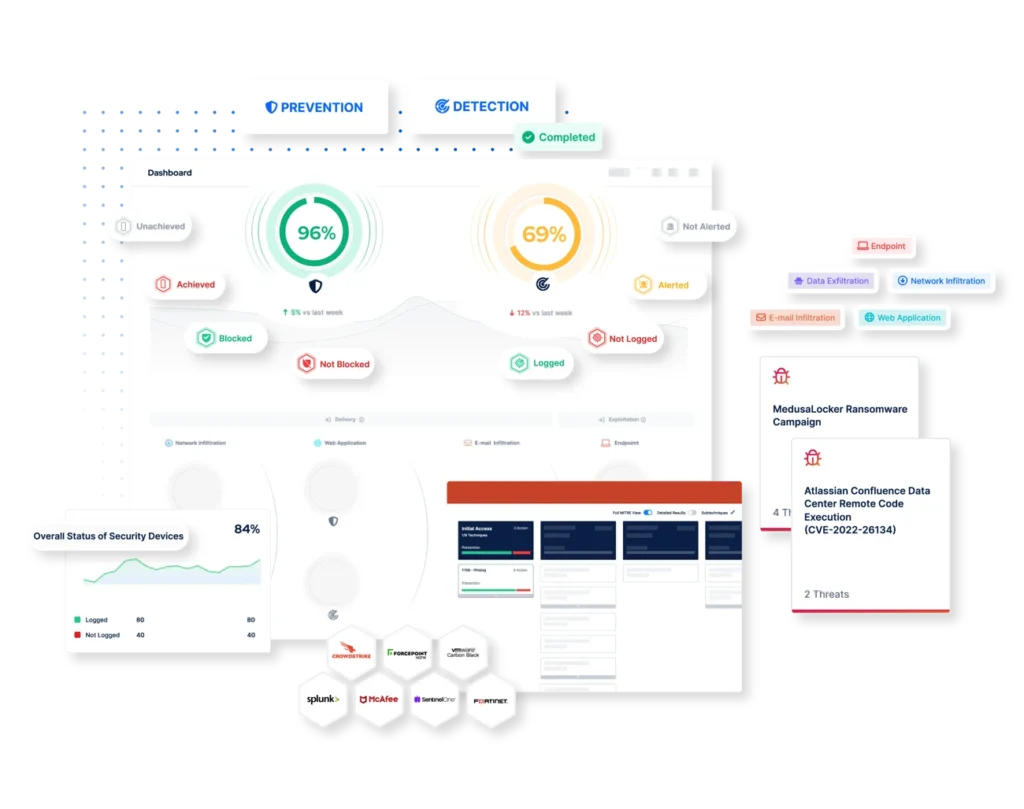
Security controls validation leverages breach and attack simulation (BAS) to put your defenses to the test. Using an extensive library of real-world threats, these simulations measure how well your endpoint and network security tools can prevent and detect malicious activity. But this isn’t just guesswork—the entire process is grounded in the MITRE ATT&CK framework, an industry-standard model for understanding adversary tactics and techniques.
Here’s how it works:
Simulate Real Threats: The BAS platform runs simulated attacks mapped to the MITRE ATT&CK framework.
Measure Effectiveness: Your security tools are evaluated for their ability to prevent or detect these threats.
Get Scored: You receive prevention and detection scores, showing how effective your controls are.
Compare with Peers: Your scores are benchmarked against others in similar industries to provide actionable insights.
Why Peer Comparisons Matter
Without context, a score can only tell part of the story. For example, a detection rate of 85% might sound impressive, but what if your industry peers are averaging 95%? Understanding how you measure up helps prioritize improvements and justifies investment in security enhancements.
Peer comparisons also:
Highlight gaps in prevention and detection capabilities.
Provide confidence to stakeholders that your controls are aligned with industry standards.
Support compliance efforts by demonstrating proactive security measures.
Built for Actionable Insights
Our security controls validation process doesn’t just stop at delivering scores. It provides a roadmap for improvement, detailing which threats your defenses struggled with and how to strengthen them. This makes the data not just informative, but transformative.
Closing the Gap
Every organization faces unique challenges, but no one operates in isolation. By comparing your prevention and detection capabilities to your peers, you gain critical insight into where you excel and where there’s room to grow.
Ready for Cyber Resilience?
Are you ready to take the guesswork out of cybersecurity? With breach and attack simulation built on the MITRE ATT&CK framework, you can validate your security controls, gain meaningful benchmarks, and strengthen your defense posture against today’s most sophisticated threats.
Want to learn more? Let’s talk about how we can help you stay ahead of the curve.

